This article is co-authored by BenFen × TX-SHIELD.

Privacy Payments Must Become Native Infrastructure at Chain-Level
In today’s blockchain ecosystem, privacy is often treated as an optional add-on—implemented through standalone DApps or Layer 2 protocols. While this “plug-in” approach offers flexibility, it frequently introduces performance bottlenecks, ambiguous compliance boundaries, and fragmented user experiences.
The core thesis and product positioning of BenFen Chain is to fundamentally redefine privacy payments as a native, chain-level capability, directly embedded into the base layer of the public blockchain. Under this design, privacy is no longer an optional feature that requires additional integration or repeated transaction fees. Instead, it becomes a foundational service and platform-level capability that all upper-layer applications—particularly those within the stablecoin ecosystem—can invoke by default.
From TX-SHIELD’s design perspective, the significance of this approach lies in treating privacy not merely as a technical optimization, but as a foundational settlement primitive. Privacy, in this view, must be embedded at the protocol level to protect sensitive financial information while remaining verifiable, auditable, and compatible with institutional and regulatory requirements.
BenFen’s privacy payment functionality will be deeply integrated with its ecosystem application BenPay, and will interoperate with native on-chain features such as stablecoin-based gas payments, sponsored transactions, and one-click issuance of real-world assets (RWAs). BenPay will comprehensively incorporate privacy capabilities across payments, trading, and account systems, providing standardized interfaces for cross-border settlement, everyday consumption, and payment scenarios, thereby accelerating the inclusive adoption and large-scale deployment of privacy payments.
At the same time, through its collaboration with core infrastructure provider TX-SHIELD, BenFen Chain natively embeds privacy mechanisms based on Multi-Party Computation (MPC) at the protocol level. This architecture delivers a new class of stablecoin settlement solutions for enterprise users—one that achieves high performance, compliance, and strong privacy guarantees simultaneously.
| TX-SHIELD is a technology company specializing in privacy payment algorithms, delivering regulator-friendly and privacy-preserving, end-to-end solutions for public blockchains, stablecoin issuers, and decentralized exchanges (DEXs). www.tx-shield.com |

Why Must Privacy Payments Be Native at the Chain Level? The Performance–Security–Compliance Trilemma
Embedding privacy logic directly into the blockchain base layer is not merely a technical implementation choice. It is a deliberate response to the intertwined requirements of performance, security, compliance, and commercialization.
TX-SHIELD takes the view that privacy-preserving settlement must be verifiable and regulator-compatible by design; otherwise, privacy systems will remain fundamentally incompatible with institutional adoption.
- Unified Performance and Cost: Eliminating the Overhead of “Plug-Ins”
Traditional add-on approaches, such as Layer 2 privacy protocols or mixers, typically require users to pay multiple fees and tolerate additional latency when assets move across chains, zero-knowledge proofs are generated, or cryptographic signatures are produced.
- By unifying privacy computation logic with the transaction settlement mechanism at the chain level, gas fees can be fully consolidated. This enables true “single-settlement, end-to-end privacy”, avoiding the fragmentation of proof or signature costs across cross-chain or off-chain workflows that otherwise introduce repeated fees and delays.
- Such native integration directly satisfies the rigid enterprise-grade requirements for high performance and low costs.
- Stronger Security and “Controlled Privacy”
Chain-level native capabilities allow for deep integration of node governance, remote attestation, and audit interfaces. This not only reinforces trust under a decentralized security model, but also enables a critical architectural principle: controlled privacy.
- Privacy execution remains protected by decentralized guarantees, while still supporting controlled pathways for selective disclosure when compliance requirements arise.
- Users and institutions can, when necessary, present audit proofs or regulatory information to authorized entities through selective disclosure mechanisms—achieving a practical balance between privacy preservation and regulatory obligations.
- Regulatory-Friendly by Design
As global financial institutions continue to raise standards for compliance and risk management, compliance costs have become a major constraint on the large-scale adoption of Web3 systems.
- A chain-level native architecture allows compliance interfaces,such as selective disclosure, regulatory views, and audit credentials, to be designed in parallel with privacy functionality from the outset.
- This compliance-friendly native system significantly reduces backend integration complexity and regulatory friction, lowering both the compliance costs and onboarding barriers for institutional users.
Architectural Comparison: Chain-Level Native vs. Layer 2 vs. Plug-Ins
| Feature | BenFen: Chain-Level Native Privacy | Layer 2 / Standalone Privacy Protocols | Wallet Plug-ins / Mixers |
| Positioning / Use Cases | B2B / Enterprise-grade settlement | Rapid iteration, scalability | Individual, ad hoc privacy needs |
| User Experience / Settlement | Excellent UX; unified fees and settlement | Fragmented UX; frequent bridging | Limited experience |
| Compliance | Embedded compliance interfaces; controlled disclosure | Cross-protocol compliance requires bridges; higher complexity | Significant regulatory gaps; high regulatory risk |
| Core Strengths | High efficiency, auditability, enterprise-grade trust | Strong scalability | Fast deployment, but fragmented user experience |
Stablecoins and Privacy Payments: Two Sides of the Same Coin and Their Inevitable Convergence in Digital Value Circulation
From the long arc of monetary history, TX-SHIELD observes that every major transition in payment paradigms has been driven by the renewed satisfaction of two fundamental demands: the stability and credibility of value, and the freedom and security of transactions. This pattern holds true from physical currency to bills of exchange, and later to electronic payments. Today, we stand at the threshold of the next payment revolution. The deep integration of stablecoins and privacy payments is the key to opening this door. This is not a simple combination of two independent technologies, but rather an inevitable convergence of two inseparable dimensions within the digital value circulation system. According to TX-SHIELD’s design philosophy, the convergence of stablecoins and privacy payments is not optional, but an inevitable requirement for achieving scalable and institution-grade digital value circulation. Stablecoins are emerging as the new global standard for payments and settlement, while privacy protection fulfills the non-negotiable requirement of transactional freedom. Like two sides of the same coin, they jointly define the future form of payments.
Historical Inevitability: Why Convergence Is the End State of Digital Payments
The foundation of the digital economy lies in the ability for value to flow through global networks with the same efficiency and minimal friction as information itself. Yet existing solutions all suffer from structural limitations:
- Traditional electronic payments: rely on centralized intermediaries. Cross-border transactions are expensive, and user data is monopolized by platforms, leaving little room for meaningful privacy protection.
- Stablecoins on transparent blockchains: as on-chain representations of fiat value, address the most fundamental problems of value measurement and settlement in the digital economy. They enable payments that are efficient, low-cost, and globally accessible. Stablecoin transaction volumes already account for a significant and continuously growing share of total on-chain activity, with particularly strong adoption in enterprise settlement and cross-border payment scenarios. However, value stability alone does not equate to complete trust. In fully transparent and traceable on-chain ledger environments, every transaction risks exposing commercial confidentiality. Advanced on-chain analytics tools can, within a very short transaction process—or even just a few key ones—accurately infer an enterprise wallet’s business model, operating costs, and even strategic procurement and clearing behaviors, creating substantial competitive risks for businesses.
- Privacy coins: they address confidentiality concerns, but due to high price volatility and the lack of broad value anchoring, they are unable to function as reliable units of account or settlement media for payments.
As a result, history points toward an inevitable path: the native integration of stablecoins is the most effective payment instrument, with privacy payments, which safeguard transactional freedom. This convergence represents the unavoidable trajectory toward the maturation of payment systems in the digital era.
1 + 1 > 2: How Integration Creates a New Paradigm Beyond Any Single Technology
When stablecoins and privacy payments are deeply coupled at the base layer of BenFen Chain, the resulting synergy goes far beyond a simple addition of features.
From “Compliance Cost” to “Compliance Advantage”
From TX-SHIELD’s architectural perspective, traditional privacy solutions often conflict with regulatory requirements, forcing a difficult choice between “transparent exposure” and “non-compliant privacy”. By natively integrating privacy payments and stablecoins at the chain level and embedding a controlled privacy mechanism, BenFen Chain enables enterprises to conduct fully compliant stablecoin payments while protecting transaction details by default. Only when required by regulators—such as during audits or judicial investigations—are proofs provided through selective disclosure mechanisms. This architectural shift transforms privacy from a perceived “compliance risk” into a “compliance and business competitive advantage”.
From “Limited Use Cases” to an Ecosystem of “Unlimited Possibilities”
The convergence of stablecoins and privacy payments unlocks a wide range of business scenarios that were previously impractical due to privacy constraints or payment inefficiencies:
- A Paradigm Shift in Global Payroll and Supply Chain Finance
Multinational enterprises can use stablecoins to distribute salaries to employees worldwide in real time, protecting personal privacy while leveraging programmability for customized financial processing. Within supply chains, core enterprises can establish “auditable privacy settlement networks”, where stablecoin transaction flows between upstream and downstream participants are encrypted from the public, yet the compliance of the entire network can be collectively demonstrated to regulators—significantly improving capital efficiency and risk control.
- The Institutional Upgrade of DeFi
Traditional DeFi has long been criticized by institutions for the transparency of trading strategies. On BenFen Chain, a new class of “privacy-first”, institution-grade DeFi can emerge—such as confidential lending protocols and DEXs designed to prevent frontrunning and MEV exploitation. Large institutional capital can enter the ecosystem while safeguarding strategic intent, bringing unprecedented depth and liquidity to DeFi markets.
- Next-Generation Consumer Applications and the Data Sovereignty Economy
Users can pay for subscriptions and purchase digital goods with stablecoins, while their consumption patterns, identity data, and asset holdings remain effectively protected—realizing the principle of “payments as a service, without data exhaust.” This lays the foundation for Web3 business models built on genuine data sovereignty.
Stablecoins and privacy payments are the two core engines driving on-chain economies toward maturity and large-scale adoption. The distinctive positioning of BenFen Chain lies in its deep coupling of these two engines, creating a public-chain infrastructure purpose-built for high-frequency, high-value payment scenarios. Choosing BenFen Chain means choosing a compliant, secure, and high-performance stablecoin payment ecosystem,and stepping directly into the next phase of digital payments.
BenFen Chain: The “Highway” Born for Privacy Payments
Building a blockchain network capable of supporting large-scale, enterprise-grade privacy payments requires overcoming the performance overhead and economic friction introduced by privacy computation at the base layer. The full-stack system, co-developed by BenFen Chain and TX-SHIELD—spanning programming languages, consensus mechanisms, and economic models — is designed to systematically remove these barriers, establishing a triple foundation of security, efficiency, and usability for institutional privacy payments.
3.1 Move Language: “Mathematical-Level Trust” for Privacy Assets
The core of privacy payments lies in safeguarding on-chain assets and ensuring the correct execution of operations. BenFen Chain adopts the Move programming language, designed specifically for digital assets, providing security guarantees far beyond comparable languages at the foundational level.
- Intrinsic Security Guarantees: Move’s strict type system and unique resource management mechanism prevent common, critical smart contract vulnerabilities—such as reentrancy attacks or resource exhaustion—at compile time. This ensures that the core contract logic governing privacy assets is rigorous, and that asset states remain precise and well-defined.
- Reliability Assurance: Through the Move Specification Language (MSL), smart contracts can explicitly define preconditions, postconditions, and invariants, describing from the source level how the program should behave correctly. During compilation, these specifications are translated into Boogie language expressions and verified by an automated theorem prover. This process allows contracts to be mathematically validated for safety and correctness before deployment, minimizing runtime errors and vulnerabilities, and creating an on-chain execution environment that is verifiable, predictable, and trustworthy.
3.2 High-Performance Consensus: Harnessing Computing Power to Overcome the “Performance Tax” of Privacy Computation
Privacy computation inherently introduces computational overhead and latency. To support high-frequency commercial use cases, top-tier performance is essential. BenFen Chain’s innovative DAG-based hybrid consensus successfully addresses this challenge.
- Sub-Second Latency and Tens of Thousands of Transactions Per Second: By differentiating transaction types, transactions that do not involve shared objects are processed via a “fast path”. This enables transaction processing times under 0.5 seconds and sustained throughput of 10,000+ TPS. Such performance ensures that even computation-intensive privacy transactions feel “instantaneous”, fully meeting the real-time requirements of commercial settlement.
- Exceptional Robustness and Availability: The consensus mechanism provides high fault tolerance, allowing the network to operate stably even if some validator nodes fail. This 24/7 uninterrupted availability is a key factor in delivering privacy payment services with reliability comparable to traditional financial infrastructure.
3.3 Stablecoins as “First-Class Citizens”: Eliminating Economic Friction
One of the most revolutionary design features of BenFen Chain is the elevation of stablecoins to “first-class citizen” status at the public chain level. This serves as the economic foundation for removing user barriers and enabling large-scale adoption.
- Native Integration, Payments with Privacy by Default: Privacy payments operate directly on BenFen Chain’s native stablecoins, without the need for complex cross-chain bridges or wrapped assets. This achieves atomic-level integration of payment and privacy at the chain layer, completely eliminating intermediary steps that introduce additional security risks and friction.
- Web2-Level Smoothness: Users can pay transaction fees directly in stablecoins, without needing to acquire or hold native tokens for gas in advance. This design lowers the entry barrier for privacy payments to a minimum, delivering a user experience as seamless and intuitive as Web2 tools, and is key to driving large-scale commercial adoption.
3.4 Modularity and Universality: Flexibility for the Future Privacy Payment Ecosystem
Leveraging the modular design and advanced abstraction capabilities of the Move language, BenFen Chain provides high flexibility and reusability for the development of upper-layer privacy payment applications.
- Secure Modular Reuse: Developers can reuse formally verified security modules like building blocks, enabling rapid construction of complex privacy payment logic.
- Universality and Future Compatibility: Although BenFen Chain centers on stablecoins, its underlying architecture and Move modules support general-purpose privacy payment capabilities, compatible with any type of asset. This flexibility ensures that the infrastructure not only meets current stablecoin payment needs but also adapts to evolving commercial scenarios and future innovations.
BenFen Chain is not a public blockchain with privacy as an afterthought. It is an infrastructure deeply customized for privacy payments. Its full-stack technology choices—from the secure Move language, high-performance DAG consensus, to frictionless native stablecoin integration—together form a top-tier foundation that delivers comprehensive support for security, performance, usability, and user experience, enabling the next generation of privacy payments.
How BenFen Chain Enables Privacy Payments
BenFen Chain’s privacy payment functionality, developed in collaboration with TX-SHIELD, is designed to provide users with a seamless experience while ensuring the confidentiality of critical information. The design implements a complete closed loop—from the private creation of assets, to secure value transfer, and finally to controlled viewing and redemption. Through technical integration with TX-SHIELD, privacy protection becomes a foundational feature of the payment system, rather than an add-on.
Creation of Privacy Assets: One-Step Privacy from Deposit
BenFen Chain’s architecture preconfigures privacy options, allowing users to decide whether to deposit tokens in privacy form at the moment of funding, eliminating multi-step processes and providing a smoother experience.
Detailed Process:
- Initiate a Privacy Deposit or Privacy Token Conversion:
When selecting a token to deposit in the wallet, users can simply check the “Deposit as Privacy Token” option. Alternatively, users can initiate an “Asset Encryption” transaction through their wallet, specifying the tokens and amounts they wish to convert into privacy form.
- Asset Locking:
Once the transaction is confirmed by the network, a specialized smart contract automatically locks the converted tokens, providing the value backing for the soon-to-be-created privacy asset.
- Value Sharding:
Network validator nodes receive the value and use their internal shared keys and encryption algorithms to convert it into a set of unique, non-patterned data shards.
- Proof Generation:
The system creates a new “privacy asset” object for the user and stores the newly generated data shards within it.
- Completion:
After the transaction is recorded on-chain, the user’s public tokens are locked, and an equivalent privacy asset exists in encrypted shard form, with its real value no longer visible on-chain.
This “deposit-to-privacy” mechanism eliminates the barrier to acquiring privacy assets, making privacy protection the default option for on-chain operations rather than a complex, additional process.
Privacy Payments
Once users hold privacy assets, they can make payments without exposing transaction details. The following example illustrates the core process when User A pays User B:
- Transaction Construction:
User A’s wallet creates a transaction, specifying B as the recipient and setting the payment amount. It then sends an authorization request to a trusted validator node, requesting that the payment amount be processed into temporary encrypted shards.
- Network Submission:
The wallet packages all necessary information to execute the transaction and submits it to the network. The transaction includes A’s current balance shards, B’s current balance shards, and the encrypted shards representing the transaction amount obtained in the previous step.
- Backend Computation:
Upon receiving the transaction, the network validator nodes use shared keys to decrypt and compute the three sets of shards. The results are then re-encrypted into new encrypted shards.
- State Update:
The computation generates two sets of new data shards—one representing A’s updated balance and the other representing B’s updated balance. These new shards are then updated in the respective privacy asset objects of A and B.
- Transaction Completion:
Once the transaction is recorded on-chain, the value transfer is complete. To other on-chain users, they can observe that the privacy asset objects of A and B have changed, but the specific transaction amount remains undisclosed.
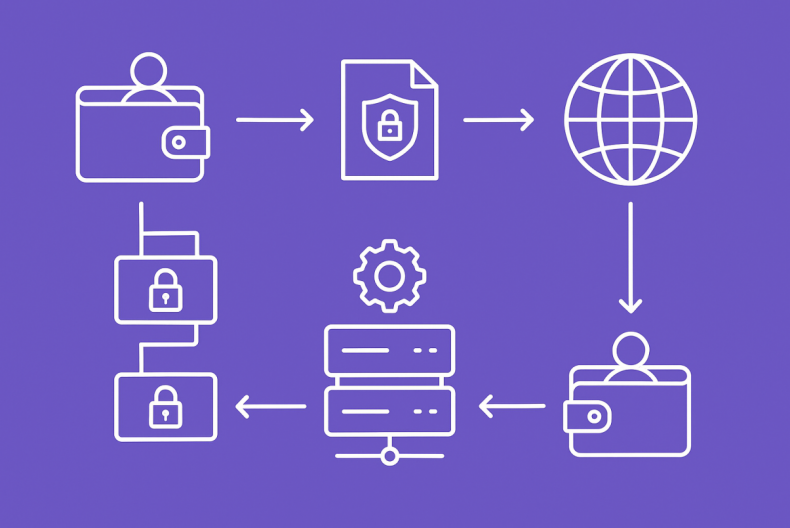
Viewing and Redeeming Privacy Assets
- Initiate Request and Sign:
Users send a request to a trusted network node via their wallet. The request includes a digital signature generated with the user’s private key to prove ownership.
- Identity Verification:
Upon receiving the request, the node verifies the signature to confirm that the requester is the legitimate owner of the privacy asset as recorded on-chain. This step prevents unauthorized access by other users.
- Off-Chain Reconstruction:
Once verified, the trusted node reads the encrypted shards of the user’s asset from the chain and reconstructs the actual balance in its local memory using shared keys, making it readable for the user.
- Secure Return or Redemption:
- Viewing: The reconstructed balance is securely sent back to the user’s wallet front-end through an encrypted channel for display.
- Redemption: Users can authorize a transaction to destroy their privacy asset credentials on-chain. Once the network confirms the destruction, the original amount of locked public tokens is automatically released and returned to the user.
BenFen Chain’s privacy payment system forms a complete, verifiable, and regulator-friendly privacy payment loop through three stages: deposit-as-privacy, encrypted shard circulation, and controlled transparent redemption. This system is not an external plug-in or protocol-layer add-on; it is a native, base-layer capability of the public chain. It makes privacy protection the default option, ensures stablecoin settlements are confidential by design, and allows enterprises and individuals to achieve truly private payments under compliance constraints. On BenFen Chain, privacy is no longer an “extra safeguard”; it is an integral part of payment itself.
Core Technologies of BenFen Chain Privacy Payments
From TX-SHIELD’s system design perspective, privacy preserving settlement must be constructed as a verifiable cryptographic process rather than a black-box execution environment, ensuring both confidentiality and auditability at scale.
Confidential transaction system architecture is based on FAST MPC and regulatory Intervention.
BenFen Chain’s privacy payments, developed in collaboration with TX-SHIELD, represent a systematic innovation that integrates blockchain technology (Block Node), Fast Multi-Party Computation (FAST MPC), and regulatory compliance mechanisms (Regulator). This architecture enables “data usable but not visible” asset transfers within a distributed network, combining confidentiality, compliance, and operational efficiency in a unified system.
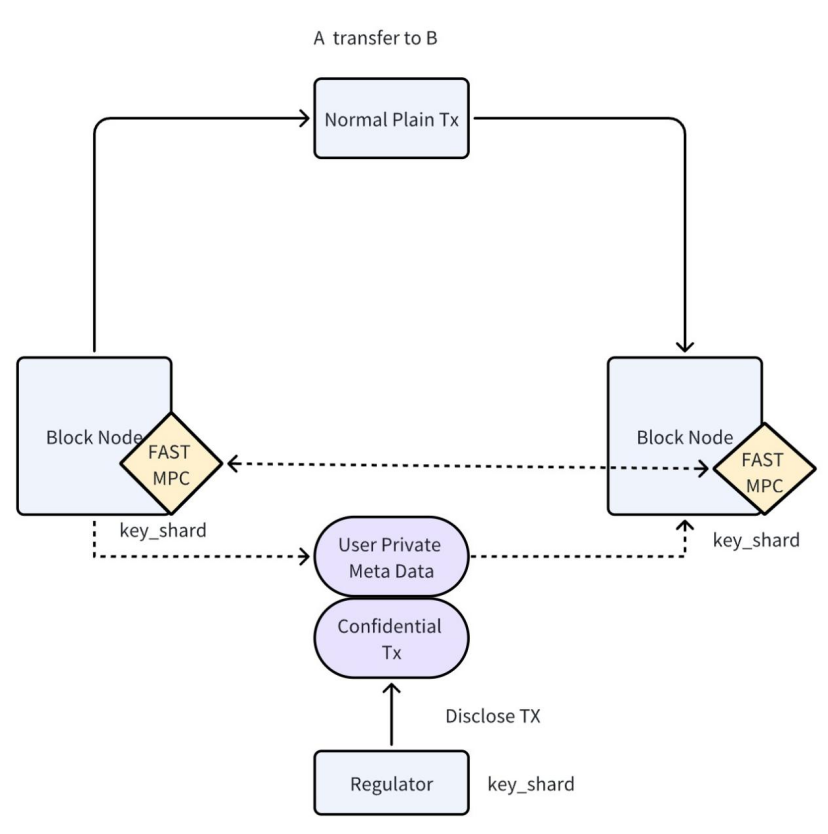
I. Core System Objectives
The primary goal of the system is to resolve two fundamental tensions in traditional blockchain transactions: privacy protection and regulatory compliance. Privacy Protection: The system ensures that when User A transfers assets to User B, sensitive information such as transaction amounts and participant identities is never exposed in plaintext on-chain, maintaining the confidentiality of transaction details. Regulatory Compliance: While protecting privacy, the system also incorporates mechanisms that allow authorized regulators to securely and controllably access and audit transaction details under specific circumstances. The specific implementation of this functionality through FAST MPC will be detailed in subsequent sections. Currently, in the released version, all privacy payments on BenFen Chain are implemented using MPC. However, a more advanced and versatile version, combining MPC and Fully Homomorphic Encryption (FHE), will be gradually introduced in future iterations, offering enhanced functionality and greater flexibility.
II. Key Technical Components
The system consists of several core components: Block Node, Fast Multi-Party Computation (FAST MPC), and Key Shards (Key_shard). The following provides an overview:
- Block Node
The Block Node serves as the core of the distributed ledger system, responsible for transaction validation, consensus, and storage. All transactions—whether Plain TX or Confidential TX—must be processed by these nodes.
- Fast Multi-Party Computation (FAST MPC)
FAST MPC is the core technology for achieving privacy protection in the system. MPC allows participants to jointly compute a predefined function without revealing their individual inputs. The term “FAST” emphasizes that this MPC scheme has been optimized for performance and efficiency, meeting the high-throughput requirements of blockchain networks. The MPC module runs within the Block Node and primarily handles Key_shards and User Private Meta Data, used for generating or verifying confidential transactions. In the initial version of BenFen Chain, FAST MPC’s functionality is relatively limited. However, through research conducted by STL, more advanced MPC versions integrating other cryptographic protocols such as Fully Homomorphic Encryption (FHE) have been explored. These enhanced versions provide additional functionality, increase transaction privacy and security under regulatory constraints, and enable faster and more convenient batch operations.
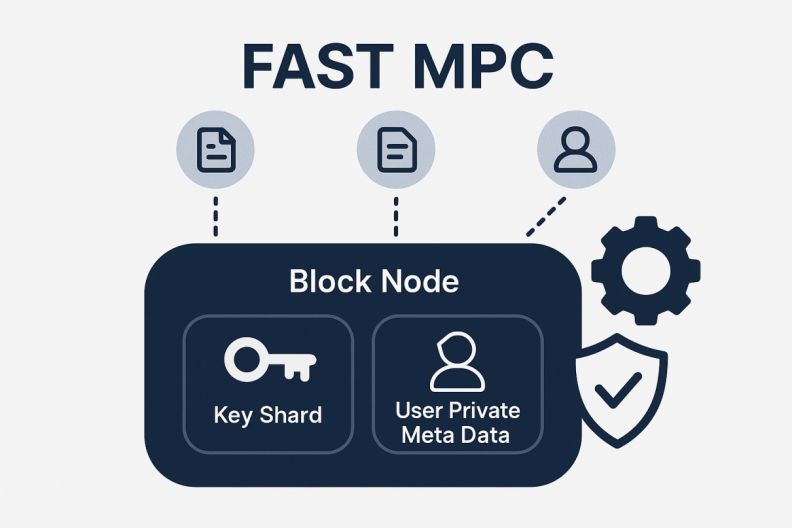
- Key Shards (Key_shard)
Key Shards are critical for data security and regulated access, and are generated by the FAST MPC module. A user’s private metadata is encrypted or split into multiple key shards, which are held by different entities (e.g., Block Node and Regulator). Only by combining Key_shards from different sources (e.g., from the Block Node and the Regulator) can the core User Private Meta Data be accessed or decrypted.
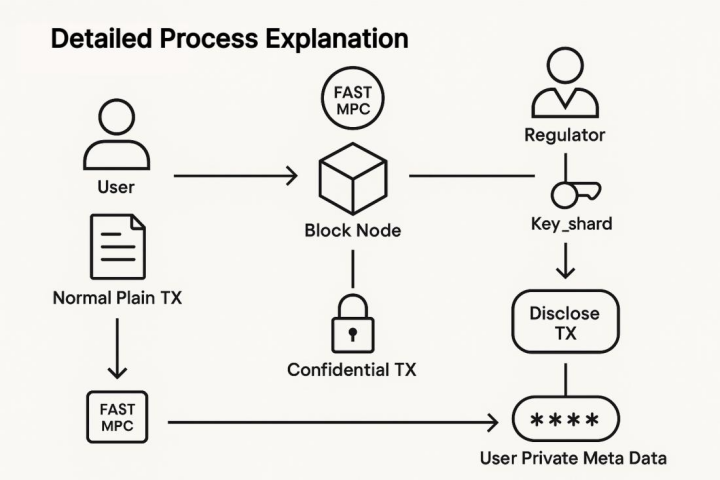
III. Detailed Process
- Initiate a Normal Transaction: The user initiates a Normal Plain TX to transfer assets.
- Generate Confidential Transaction: The transaction enters the Block Node. The system’s FAST MPC module uses its held Key_shards to process the User Private Meta Data, producing an encrypted Confidential TX. This confidential transaction is then sent back to the Block Node for on-chain recording.
- Regulatory Intervention Point: The Regulator is a special participant in the system and holds Key_shards.
- Transaction Disclosure: When a transaction requires regulatory review or audit, the Regulator initiates a Disclose TX request. This request combines the Regulator’s Key_shard with the User Private Meta Data. Specifically: a. The Regulator’s shard combines with the Block Node’s shard to reconstruct or access the User Private Meta Data. b. Only when the regulatory process is triggered and the Regulator’s authority is verified can the contents of the Confidential TX be conditionally and controllably disclosed via MPC or decryption mechanisms.
Highlights and Differentiated Advantages of BenFen Chain Privacy Payments
As blockchain moves toward mainstream adoption, privacy and user experience are often difficult to reconcile. BenFen Chain elevates privacy payments from an “optional feature” to a native, chain-level capability. Through a combination of protocol-level and product-level innovations, it significantly lowers the adoption barrier while meeting institutional compliance requirements. The following outlines the core highlights and differentiated advantages of BenFen Chain’s privacy payment system.
Comprehensive Privacy Protection
Privacy protection on BenFen Chain extends beyond asset amounts to encompass all sensitive dimensions of a transaction, leveraging cryptographic primitives to provide tiered protection.
- Full Transaction Data Obfuscation
- Core Technology: Deeply integrated MPC protocols and zero-knowledge proofs. Transaction initiators collaborate with participants off-chain using MPC to generate the transaction. During this process, all critical fields—including input/output amounts, sender/receiver addresses, and asset types—are converted into encrypted states or commitments, with only the final valid state changes committed to the blockchain. Network nodes can verify the correctness of state transitions but cannot infer any underlying transaction details, effectively eliminating the possibility of on-chain data analysis.
- Batch Privacy Transactions and Collective Settlement
- Core Technology: MPC batch processing with verifiable encryption and aggregate signatures. By embedding verifiable random functions into the MPC protocol, a batch of transactions is assigned a single, batch-verifiable anonymous identifier. Validators can then verify the legality of the entire batch in one operation, rather than processing each transaction individually.
- Private Asset Transfers
- Core Technology: Key-based encryption and access control. Each encrypted transaction record is associated with one or more symmetric/asymmetric keys. Only participants holding the corresponding decryption keys can access the transaction details. This restores data ownership, ensuring that transaction records are private journals accessible only to relevant parties, rather than public ledger entries.
- Temporarily Authorized Visibility
- Core Technology: Attribute-based encryption (ABE) or proxy re-encryption. When transaction information needs to be provided to auditors, regulators, or judicial authorities, the key owner can grant access without exposing all private data. By generating a time-limited, scope-specific access token or performing a one-time proxy re-encryption, a third party can decrypt designated transactions for a specified period. Access automatically expires once the authorization period ends.
Built-In and Programmable Regulatory Compliance
Regulatory compliance on BenFen Chain is not an after-the-fact external add-on, but a core, protocol-level feature designed to balance privacy protection and regulatory oversight.
- Selective Disclosure
- Core Technology: Zero-Knowledge Proofs (ZKP) and layered key systems. Different transaction attributes are encrypted and controlled by separate keys or ZKP systems. Users can selectively disclose specific information according to regulatory or business requirements, without exposing all data. For example, a user can prove to a tax authority that a transaction amount meets a threshold without revealing counterparty details.
- Enterprise-Grade Audit Node Authorization
- Core Technology: Threshold signatures and dynamic permission management. Enterprises can predefine audit policies, distributing access keys for certain transaction data to designated audit nodes in a threshold manner via smart contracts or off-chain protocols. Keys can only be reconstructed and accessed when predefined conditions are met, ensuring internal governance while preventing abuse of unilateral power.
- Protocol-Level Embedded Compliance Interfaces
- Core Technology: Modular cryptographic suites and standardized regulatory APIs. MPC, FHE, ZKP, and other cryptographic components are integrated into consensus mechanisms and state transition functions, rather than invoked as external APIs. Regulatory rules can be executed through verifiable computation either off-chain in the MPC phase or on-chain in smart contracts, ensuring compliance checks are automated without leaking private data.
- Legally-Governed Decryption Threshold Mechanism
- Core Technology: Distributed key generation and threshold decryption. The system predefines a regulatory public key controlled by multiple parties, with the corresponding private key split and held in a threshold manner. Only upon obtaining a legitimate judicial order can these independent parties collaboratively execute the threshold decryption protocol to reconstruct the master key and decrypt the transaction history of specific addresses. This process is transparent, auditable, and multi-party, preventing unilateral surveillance.
High-Performance Architecture and Implementation
Through cryptographic innovations and system architecture optimizations, BenFen Chain addresses the performance bottlenecks of traditional privacy technologies.
- Enhanced MPC and Advanced Cryptography Fusion Architecture (Planned Implementation)
- Core Technology: FHE-MPC hybrid model and recursive composition proofs. A layered cryptographic architecture is planned: At the base layer, Fully Homomorphic Encryption (FHE) enables computation on encrypted data, ensuring that data remains encrypted throughout the process. At the upper layer, MPC protocols coordinate FHE computations and handle complex logic and conditional operations. Recursive zero-knowledge proofs aggregate multiple transactions or state updates into a single, compact proof, significantly reducing on-chain storage and verification costs, achieving fully encrypted sharding and recovery.
- Second-Level Privacy Confirmation Time
- Core Technology: Currently, all computations are performed online, but future implementations will adopt a two-phase offline/online computation with pipelining optimizations. Most computation-intensive operations are completed offline, leaving only lightweight verification, signing, and consensus tasks for the online phase. This design decouples on-chain confirmation time from transaction complexity, allowing second-level confirmations regardless of backend computation load. Benchmark tests indicate that, on standard commercial hardware, the system conservatively supports 1,000+ privacy transactions per second, with potential orders-of-magnitude performance improvements through algorithm optimization and hardware acceleration—fully meeting the needs of high-frequency financial applications.
Internal benchmarks suggest the architecture is capable of supporting high-throughput privacy transactions, with significant scalability potential as optimizations continue.
Exceptional User Experience
Privacy features in traditional blockchains are often “add-on” solutions, requiring users to learn extra operational steps. BenFen Chain, however, is designed to make privacy protection a seamless, default experience.
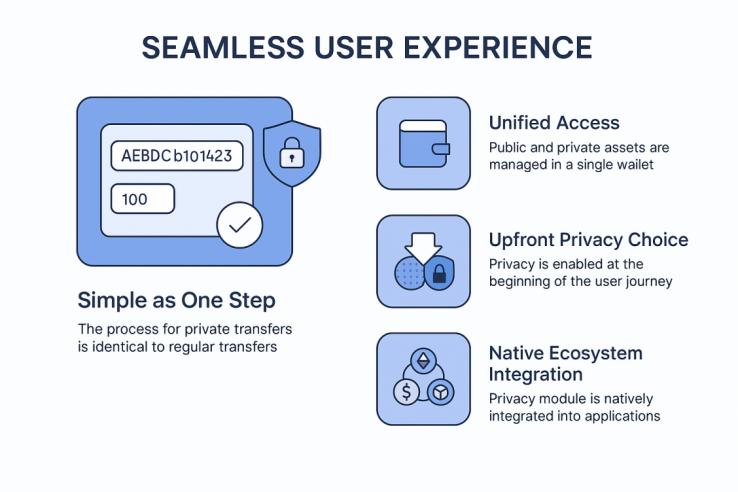
Simple, One-Step Operations: Performing a privacy transfer is identical to a regular transfer. Users simply enter the recipient address and amount in their wallet and confirm—the privacy protection is automatically executed in the background, eliminating the need for additional learning. This design aligns with industry efforts to enhance blockchain usability.
Unified Entry Management: Users do not need multiple wallets or plugins. Both public and privacy assets are managed seamlessly under a single wallet address, with balances easily viewable at any time. This unified approach greatly simplifies asset management.
Preconfigured Privacy Choice: Designs such as “Deposit-as-Privacy” move the privacy selection upfront to the deposit stage, making privacy protection the starting point of the user journey, rather than an after-the-fact option.
Native Ecosystem Integration: Upper-layer applications—including the BenPay ecosystem, RWA issuance, and DeFi protocols—can natively invoke privacy modules for seamless access. For example, in BenPay DeFi Earn, deposits, share changes, and redemptions are all processed through BenFen’s native privacy modules. Operations are provably correct, yet external observers cannot see user positions, yield amounts, or rebalancing activity, making BenPay DeFi Earn a privacy-protected DeFi entry point. With BenPay Card, online or offline payments encrypt amounts, payment paths, and account information, ensuring merchants cannot view on-chain asset holdings and observers cannot construct spending profiles. This delivers privacy-preserving stablecoin payments and a truly usable Web3 consumer experience.
Thanks to Layer 1 native privacy design, the ecosystem maintains a consistent, seamless privacy experience across payments, trading, consumption, and asset management.
BenFen Zero Gas Fee Experience
Gas fees are one of the major barriers for ordinary users entering the Web3 world, especially when using computationally intensive privacy features. BenFen Chain redefines transaction cost structures through protocol-level innovations.
Sponsored Transactions: At the protocol level, BenFen Chain separates the roles of “transaction initiator” and “gas payer”. This allows projects or merchants to directly cover gas fees for users, in a process that is simple, secure, and efficient. For users, this means they can use privacy payments without worrying about or paying gas fees.
Gas Payment with Stablecoins: Users can also pay gas fees directly using the native stablecoins within the system, without needing to hold additional tokens. This simplifies asset management and further lowers the entry barrier for privacy-enabled transactions.
BenFen Native Stablecoin Architecture
Unlike stablecoins issued via smart contracts, BenFen Chain treats stablecoins as “first-class citizens” at the chain layer, providing a robust and reliable foundation for privacy payments.
Chain-Native, Security-First: As native assets at the base layer of the public chain, these stablecoins do not rely on smart contract logic, fundamentally avoiding contract-related vulnerabilities and offering higher security.
BenFen Ecosystem Scalability
The value of a technology is determined by the vibrancy of its ecosystem. BenFen Chain’s open design lowers the entry barriers for developers and merchants.
Standardized Integration: The platform provides comprehensive SDKs and well-documented APIs, enabling third-party wallets, merchant systems, and cross-chain bridges to quickly integrate privacy payment functionality, significantly reducing development costs.
Support for Decentralized Commerce: Both centralized e-commerce platforms and decentralized DApps can rapidly deploy privacy payment modules using the tools provided by BenFen Chain, offering users a broader range of payment options. The successful integration of BenPay demonstrates the practical viability of this approach in real-world payment scenarios, providing a template for future commercial applications.
Batch Privacy Payments
For high-frequency, multi-recipient scenarios such as enterprise payroll, project airdrops, and community rewards, BenFen Chain’s batch privacy payment functionality combines efficiency with privacy.
Enhanced Efficiency: Users can distribute privacy assets to hundreds or even thousands of addresses in a single operation by selecting groups or uploading Excel templates, eliminating the need for tedious individual transactions.
Privacy and Compliance Assurance: All batch transactions are executed within a privacy-computing environment, ensuring that each transaction amount and recipient information remains fully confidential. This protects the privacy of recipients while maintaining the confidentiality of the sender’s financial data.
Privacy Payments for Any Token
Oracle Support: BenFen Chain’s privacy payment mechanism is not restricted to specific asset types. Any asset that supports the system’s settlement and accounting capabilities can be integrated into the privacy payment framework. Users can freely convert tokens into privacy-enabled forms, enabling one-click private transfers and receipts.
BenFen Chain’s privacy payment system encapsulates complex privacy technologies within a simple user experience. Its revolutionary zero gas fee model removes adoption barriers. The native stablecoin integration at the base layer establishes a foundation of security and global usability. Combined with an open ecosystem and highly efficient batch capabilities, the system extends its utility across personal and enterprise scenarios.
This represents the maturity of a complete solution that balances privacy, usability, and scalability. It is not only a technological breakthrough but also a critical step toward mainstream adoption of blockchain privacy payments.
BenFen Chain’s privacy execution capabilities are natively integrated at the chain layer based on TX-SHIELD’s underlying cryptographic architecture, forming the foundation for stablecoin privacy settlement infrastructure. As the ecosystem evolves, further enhancements in confidential execution, regulatory-compliant architecture, and enterprise-grade payment scenarios will continue to drive the large-scale adoption of privacy settlements in financial and commercial applications.
Confidential execution refers to performing settlement and state transitions over encrypted data without exposing transaction details.
TX-SHIELD is an independent privacy preserving settlement infrastructure designed to be chain-agnostic and institution-ready. BenFen Chain represents its first deep, native integration at the Layer-1 level.
About BenFen
BenFen Chain is a high-performance public blockchain specifically designed for stablecoin payments. Built on the Move programming language, it provides a secure, low-cost, and highly scalable base-layer network. A key feature of BenFen is the ability for users to pay gas fees directly with stablecoins, significantly lowering the adoption barrier and paving the way for large-scale applications.
On top of its powerful cross-chain and stablecoin settlement capabilities, BenFen Chain supports a rich ecosystem of applications covering diverse payment scenarios. More importantly, it offers enterprise users crucial privacy payment options, ensuring that while benefiting from blockchain efficiency, their core business data remains protected.
BenFen aims to become a global stablecoin circulation network serving enterprise payroll, cross-border payments, e-commerce, and offline merchants, representing a next-generation financial infrastructure that balances efficiency, cost, and security.
About TX-SHIELD
TX-SHIELD is a regulatable on-chain privacy settlement infrastructure that provides both-party privacy and regulatory-visible payment and settlement capabilities for stablecoins and blockchain applications.
Core Solution:
TX-SHIELD: A privacy settlement infrastructure for blockchain-native financial systems, enabling confidential settlement, dark pools, and protocol-layer privacy execution.
Our Innovation:
We not only protect privacy at the transaction level, but also redefine asset ownership and security through distributed cryptography. TX-SHIELD enables enterprises and financial institutions to perform joint custody, private settlement, and regulatory-compliant audits without exposing sensitive business information.
We are building an infrastructure where privacy is no longer an obstacle to regulatory compliance or institutional adoption, but a foundational protective layer for financial settlement.
TX-SHIELD — The private and regulatable settlement base layer for stablecoins, blockchain, and enterprise applications.
