The Origins of Privacy: From Human Society to the Digital Economy
Over the past century, humanity’s understanding of “privacy” has continuously evolved. It is no longer merely the “right to be left alone,” but a deeper social consensus: we have the right to determine who can access our information, to what extent, and at what time. This concept took shape long before the internet, and far earlier than blockchain.
In traditional societies, privacy was first and foremost linked to “trust.” Banks serve as a classic example: when people deposit money in a bank, they are essentially entrusting the institution with parts of their “life secrets”—their income, spending, debts, and even family structure. It is for this reason that Swiss banks established strict confidentiality systems in the last century, prohibiting any external institutions from accessing customer information without authorization. For the wealthy, this meant asset security; for ordinary people, it represented a form of respect: my finances and my information belong to me, not to the system.
Before the advent of digital currency, the most ideal tool for “privacy payments” was cash. Cash transactions leave no identity, no trace, and no database—when you hand me 100 yuan, no one else knows about it except you and me. Its anonymous nature brings both freedom and responsibility. Precisely because of this, cash has always been retained in the global financial system, symbolizing a form of decentralized trust—interpersonal credit that requires no third-party endorsement. However, as payments become increasingly electronic and networked, this anonymous freedom is gradually being eroded.
With the dawn of the internet era, data has become the new “oil.” Every click, payment, and location can be collected. We trade efficiency for “free” apps, cashless payments, and convenient cloud services, but in doing so, we also exchange our privacy. In this sense, privacy is no longer a right but a commodity to be bought and sold. In 2018, Europe introduced the General Data Protection Regulation (GDPR), requiring companies to obtain explicit consent before collecting personal data. The core logic is that privacy is not an accessory, but an individual’s ownership of their own information. However, this institutional protection remains within a centralized framework—platforms still hold data, and users can only “consent” rather than truly “control” it.
The meaning of privacy has become unprecedentedly complex in the digital world. We need to reveal our identities to participate in transactions, yet we also desire to preserve a space free from surveillance. This lies at the very heart of the digital economy’s core contradiction: systems demand transparency to prevent fraud, while individuals crave privacy for security. As a result, people are beginning to rethink how to strike a new balance between transparency and protection.
It is against this backdrop that the BenFen public blockchain stands out. It treats privacy payments as a core native capability, aiming to restore users’ control over their digital assets.
From Trust to Transparency: The Foundational Logic of Blockchain Design
If privacy represents the right to “self-determination” in human society, then transparency serves as the mechanism for building “shared trust” in the blockchain world. To understand the root of privacy’s absence in blockchain, we must return to its original design logic—why it adopted a “fully transparent” ledger structure.
In the traditional financial system, trust originates from institutions. Centralized entities such as banks, payment companies, and clearinghouses are responsible for recording and verifying every transaction. In 2008, Satoshi Nakamoto proposed a fundamentally new trust architecture in the Bitcoin whitepaper: enabling direct peer-to-peer value transfers without relying on financial institutions. Without a central authority, how can the system maintain order? The answer lies in transparency: a public ledger, verifiable transactions, and traceable history.
By leveraging consensus mechanisms and cryptographic technology, blockchain enables every node to verify transaction authenticity independently. Each transaction is packaged into a block, which is then linked in a chain-like structure via hashes, making it nearly impossible to tamper with. As a result, trust no longer relies on institutions but stems from the transparency of algorithms and the openness of rules. This design delivers unprecedented security and verifiability, forming the trust foundation of the crypto economy.
The power of transparency has been fully demonstrated in practice. The entire transaction history of Bitcoin and Ethereum blockchains is publicly accessible; anyone can verify transactions and track fund flows through a block explorer. For users, transparency ensures fairness—there are no hidden ledgers or privileged transactions; for developers, it enables smart contracts to be externally audited; for the entire ecosystem, transparency builds a common layer of trust, enabling even strangers to collaborate without relying on intermediaries. The prosperity of decentralized finance (DeFi) is a natural extension of this logic: every operation within the system can be verified, and trust is guaranteed by code rather than institutional endorsement.

The Cost of Transparency: The Reality of Privacy Deficits
Transparency comes at a cost. While the public ledger of blockchain establishes trust and security, it also conceals the profound cost of privacy loss. Every transaction and every address is permanently recorded on the chain. This “fully transparent” structure means that—if someone is willing to analyze it—they can piece together wealth distribution, behavioral patterns, and even personal identities.
In an ideal scenario, on-chain addresses are anonymous. However, in reality, the distance between anonymity and real-world identity is often just a few steps away. Analytics firms like Chainalysis and Arkham have demonstrated how techniques such as transaction clustering and address profiling can link multiple wallets to the same entity. Once combined with external data—such as social media activity, email registrations, or NFT transaction records—identities are no longer concealed.
This risk has already caused real-world harm. In a 2025 cryptocurrency kidnapping case in Manhattan, New York, an Italian man was lured by two crypto investors, then coerced into surrendering his Bitcoin wallet password. The suspects precisely used publicly available on-chain data and identity clues to deduce that the victim held substantial digital assets, thereby targeting him. Such incidents demonstrate that when wealth and transaction behaviors are publicly traceable on the chain, transparency can be exploited by criminals, posing tangible threats in the physical world.
Transparency has also introduced economic inequities. In decentralized finance, the phenomenon known as “Maximal Extractable Value (MEV)” allows certain high-frequency traders to front-run or arbitrage against ordinary users by monitoring transaction pool data. Here, transparency becomes a tool for exploitation rather than a guarantee of trust. Meanwhile, corporate on-chain activities risk exposing trade secrets, supply chain information, or compensation structures, while individual account transaction histories reveal consumption habits and investment preferences, creating new data vulnerabilities.

Thus, a transparent ledger is not an unequivocal good. It solves the “trust problem” but creates a “privacy crisis.” A growing number of users and institutions are realizing that transparent systems without privacy protection cannot support the complex economic activities of the real world. This is precisely why BenFen Privacy Payments emerged: to achieve transaction anonymity without sacrificing verifiability, enabling users to retain true privacy sovereignty on the chain. Privacy payments, therefore, are not merely a functional innovation but a necessary prerequisite for the sustainable development of blockchain—only in a system where security and privacy coexist can trust be truly solidified.
Definition and Value of Privacy Payment
Before understanding privacy payment, we must distinguish between two concepts: transaction privacy and user privacy. Transaction privacy refers to the protection of information in a single transaction. For example, in Bitcoin, coin mixing techniques can be used to hide the source of a transaction, making a specific payment untraceable on the chain. User privacy, on the other hand, is broader and involves the protection of entire accounts or user behaviors, including long-term transaction patterns, asset distribution, and identity information. Imagine an ordinary consumer: they use a digital wallet in their daily life to buy coffee, pay rent, or order takeout. If every transaction can be fully traced, not only are their consumption habits exposed, but their income status or family structure may also be indirectly revealed. The goal of privacy payments is to ensure that user behavior patterns and personal information are not permanently recorded and analyzed, while still guaranteeing transaction validity and legality.
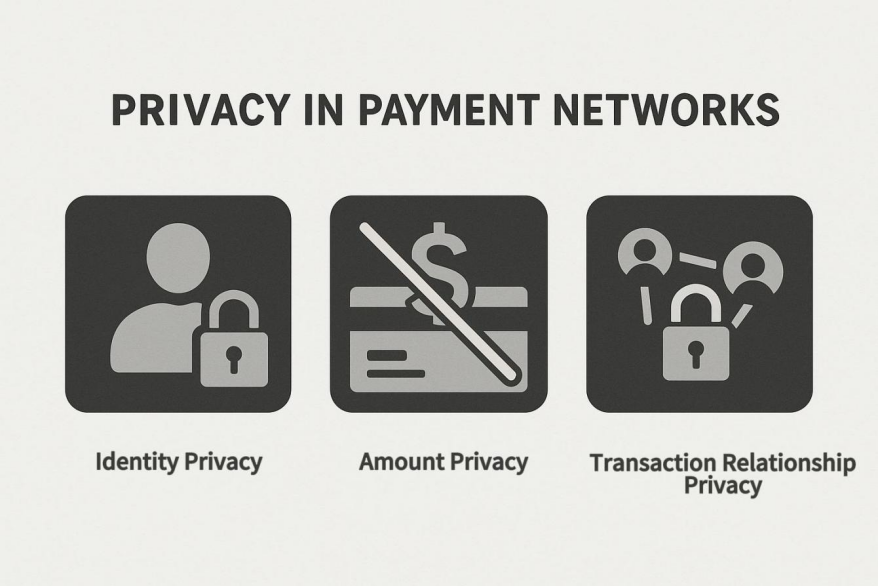
Privacy in payment networks holds value across three core dimensions. First is identity privacy—ensuring users’ identities are not directly linked to their transactions. A real-life example is when a user pays a friend or merchant, they don’t want their name, address, or contact details exposed to unrelated third parties. Second is the amount of privacy, which protects the transaction sum from being disclosed. For instance, if someone sends a digital gift or makes an investment payment, revealing the amount could lead to targeted scams or social pressure. Lastly, there’s transaction relationship privacy—preventing external analysis of transaction patterns. For example, recurring payments to a specific supplier, if traceable, could leak business strategies, supply chain layouts, or personal consumption preferences.
The social and commercial value of privacy payments is reflected across multiple dimensions. For everyday users, it reduces the risk of identity misuse or precise targeting, making digital payments safer and more liberating. For merchants and small businesses, privacy payments safeguard customer information and transaction data, preventing competitors from gleaning insights into sales volumes or supply chain arrangements. In cross-border corporate payments, privacy payments can meet regulatory compliance requirements without disclosing transaction amounts or counterparty details, thereby reducing operational costs. For example, a cross-border trading company using privacy payments to settle with overseas suppliers can avoid exposing profit margins and payment frequency while ensuring tax compliance. In daily life, when a user anonymously pays for subscriptions or online shopping through a digital wallet, they enjoy similar protections, preventing their consumption habits from being captured and analyzed by advertisers or social platforms.
Privacy payments not only help protect personal information but also enhance network engagement and trust. People are more willing to conduct transactions in a network that is secure and safeguards behavioral patterns, which directly influences the adoption rate and economic vitality of the payment network. Research shows that when digital payment users are aware that a network supports privacy protection, their willingness to use it increases significantly. This trust stems not only from technical safeguards but also from users’ awareness of their data control rights. In other words, privacy payments are not just about anonymizing individual transactions but about providing long-term, systematic protection of behavioral patterns.
Privacy payments do not imply a lack of regulatory oversight or non-compliance with legal requirements. Through zero-knowledge proofs, multi-party computation, and consent-based disclosure mechanisms, transaction networks can fulfill auditing and compliance demands without exposing sensitive information. While users benefit from privacy protection, necessary information can still be authorized for disclosure to regulators or auditors, ensuring that payment activities remain lawful, transparent, and controllable. This design not only resolves the conflict between privacy and compliance but also lays the foundation for the broad application of blockchain-based payment networks.
BenFen stands as a typical practitioner of this philosophy: its privacy payment system employs a mechanism combining zero-knowledge proofs and multi-party computation to achieve comprehensive concealment of transaction amounts, sender, and receiver addresses. At the same time, it allows regulators to conduct selective audits through a view key, ensuring compliance without sacrificing user privacy.
The Evolution of Blockchain Privacy: From Privacy Coins to Modular Infrastructure
The Era of Privacy Coins: Initial Implementation of Privacy Concepts
The earliest attempt at blockchain privacy was the emergence of privacy coins, with their core objective being to protect the identities of transacting parties and the transaction amounts. Monero, launched in 2014, was one of the first cryptocurrencies to achieve on-chain private transactions. Its core mechanisms include Ring Signatures and Stealth Addresses. In each transaction, the sender’s input is mixed with multiple historical inputs to generate a ring signature, thereby concealing the actual sender and avoiding direct on-chain linkage between the transacting parties. Recipients use one-time stealth addresses to receive funds, ensuring that payment paths cannot be directly identified by external observers. Nevertheless, if on-chain information is combined with off-chain data (such as KYC details, social media activity, or NFT transaction records), certain tracking risks may persist. Moreover, its limitations are quite evident: the transaction volume is relatively high, leading to significant blockchain bloat (with a single transaction size notably larger than Bitcoin’s). Additionally, Monero does not support complex smart contracts, restricting its usability in application scenarios like decentralized finance (DeFi).
Zcash introduced zero-knowledge proofs (zk-SNARKs) in 2016, allowing users to generate mathematically verifiable proofs of transaction validity while concealing transaction amounts and participant identities. Unlike Monero, Zcash offers a “selective transparency” mechanism that enables users to opt for shielded transactions for privacy protection. While this technology theoretically ensures both transaction validity and privacy, generating proofs requires substantial computational resources, resulting in significant transaction latency and a challenging user experience. Its early adoption rates remained relatively low, reflecting the trade-off between privacy protection and usability convenience.
The era of privacy coins laid the conceptual foundation for blockchain privacy: it explicitly introduced the philosophy of “protecting user security by concealing information,” providing both technical and ideological foundations for subsequent stages, such as protocol-layer privacy and privacy computing. At the same time, this phase also exposed the tensions between privacy protection and scalability, as well as user experience, reminding designers that a balance must be struck between privacy, security, and usability.
Protocol-Level Privacy: Meeting the Needs of Smart Contracts
With the rapid development of smart contracts and decentralized finance (DeFi), the limitations of early privacy coins in protecting privacy have become increasingly apparent. While privacy coins like Monero or Zcash effectively conceal the identities and amounts involved in individual transactions, they cannot be directly applied in scenarios such as smart contract interactions, complex asset management, and multi-transaction aggregation. To address the privacy needs of sophisticated on-chain applications, protocol-level privacy tools have emerged.
Tornado Cash is a mixing protocol on Ethereum that uses mixing pools and zero-knowledge proofs to obfuscate transaction paths, decoupling senders from receivers and making fund flows difficult to trace. It serves as a practical case study for on-chain private transactions. However, Tornado Cash also faces real-world regulatory risks: in 2022, the U.S. The Department of the Treasury added it to the sanctions list, highlighting the compliance challenges of protocol-level privacy. Additionally, Tornado Cash only supports transaction mixing and does not enable privacy operations for complex smart contracts.
In contrast, Railgun offers multi-asset private transactions and innovative contract interaction capabilities for DeFi users, supporting token types such as ERC-20 and ERC-721. Users can conceal their identities, transaction amounts, and transactional relationships while conducting on-chain activities, while also meeting certain auditing and compliance requirements through authorized interfaces. However, Railgun’s cross-chain support remains limited, primarily focused on EVM-compatible ecosystems, and its usability barrier is relatively high.
Overall, the core significance of the protocol-level privacy phase lies in enhancing privacy protection within on-chain applications, making it harder to track fund flows and user behavior in smart contracts and DeFi scenarios. The limitations of this phase primarily include operational complexity, high computational and gas costs, limited cross-chain support, and real-world regulatory risks. These constraints have paved the way for the development of subsequent privacy computing and modular privacy infrastructure, while also highlighting the inevitability of blockchain privacy technology evolving from single-transaction protection toward a verifiable, multi-functional privacy system.
During this phase of evolution, BenFen’s privacy payment feature focuses on enabling efficient on-chain anonymous transactions. It allows users to seamlessly transfer funds while concealing their identities and transaction amounts, aiming to address the convenience limitations of traditional privacy coins in mobile payments and daily use. This significantly expands the application of private coin technology in payment scenarios.
Privacy Computing Phase: Verifiability + Privacy
While protocol-layer privacy focuses more on concealing transaction data, the emergence of privacy computing has shifted blockchain from “information obfuscation” to “verifiable computation.” By performing computations on encrypted data, it ensures that data remains confidential, while the correctness of the results can still be verified. This enables privacy protection for complex smart contracts, multi-party collaborations, and cross-chain operations. Current major privacy computing technologies include zero-knowledge proofs (ZK), trusted execution environments (TEE), and secure multi-party computation (MPC). Each represents a distinct technical approach and implementation method for privacy payments, and their technical principles will be elaborated in detail later.
Trusted Execution Environment (TEE)
Trusted Execution Environment TEE:Leveraging hardware isolation mechanisms, sensitive computations are executed within the CPU’s secure enclave, making data inaccessible externally and thereby achieving hardware-level privacy. Representative projects include Oasis Network, Secret Network, and Phala Network.
Oasis Network: A Privacy-Centric Computing Platform with a Flexible Architecture
Development Timeline: The project’s mainnet officially launched in November 2020. A significant milestone was the release of the Sapphire ParaTime in 2022—an EVM-compatible privacy blockchain that significantly lowered the barrier to development.
Core Features and Architecture:
- Consensus and Execution Separation: This is Oasis’s most fundamental innovation. The network is divided into a consensus layer and multiple parallel ParaTime execution layers. The consensus layer, operated by validators, is responsible for security and stability. The ParaTime layer, run by independent node operators, handles computational tasks such as brilliant contract execution. This design enables multiple ParaTimes to process transactions in parallel, significantly enhancing scalability.
- Sapphire ParaTime: As a pivotal product in the privacy domain, it enables developers to use standard tools like Solidity to write smart contracts capable of encrypting states and processing private transactions, delivering “out-of-the-box” privacy functionality.
Applications and Ecosystem: Powered by its flexible architecture, Oasis is making significant strides in data tokenization to build a responsible data economy. Its ecosystem features notable collaborations such as co-developing data spaces with BMW Group and partnering with Nebula Genomics to safeguard the privacy of user genetic data.
Challenges: Its TEE implementation relies on specific hardware (such as Intel SGX), carrying inherent data leakage risks due to potential chip vulnerabilities. Meanwhile, its cross-chain ecosystem is still in development compared to leading public chains.
Secret Network is a smart contract blockchain characterized by its “default privacy” feature.
Development Timeline: Its predecessor, Enigma, was launched in 2017, and the mainnet went live in September 2020, making it the first blockchain with privacy-preserving smart contracts. It later enhanced its cross-chain capabilities through the launch of the Secret Ethereum Bridge.
Core Features: As the first blockchain in the Cosmos ecosystem to emphasize “default privacy,” its “Secret Contracts” ensure that contract states and input data are processed in an encrypted state, with only authorized parties permitted to view them. BenFen implements similar default privacy features on the Move VM, concealing transaction amounts and balances during transfers while providing temporary visibility authorization.
Applications and Ecosystem: The network is well-suited for privacy-focused use cases, such as confidential DeFi, private NFTs, and stealth transactions. Its ecosystem applications are natively embedded with privacy protection features from their inception.
Challenges Faced: The network faces hardware trust issues and vulnerabilities associated with Intel SGX. Furthermore, its primary challenge lies in attracting more developers and fostering a more robust ecosystem to demonstrate the broad value of “default privacy.”
Zero-Knowledge Proof (ZKP)
Zero-Knowledge Proof (ZKP) enables users to demonstrate the validity of a statement to external parties without disclosing any underlying information. Initially proposed in academia, this technology has gained widespread adoption in blockchain for privacy payments and scalability solutions. Notable implementations include Aleo and Aztec.
Aleo: Off-Chain Computing and Private Smart Contracts
Development Timeline: The project was launched in 2019, with its mainnet going live in 2024. Aleo stands as one of the earliest public blockchains to apply zero-knowledge (ZK) technology to the privacy computation layer.
Core Features: All computations are performed off-chain, with only zero-knowledge proofs being verified on-chain. This approach not only safeguards data privacy but also significantly reduces the load on the blockchain. Its dedicated programming language, Leo, enables developers to easily build applications such as privacy payments, DeFi, and identity verification, thereby lowering the barrier to development.
Applications and Ecosystem: Following the mainnet launch, community-driven projects have emerged, including privacy payment wallets, anonymous voting systems, and confidential DeFi prototype applications.
Challenges: The high computational cost of generating zero-knowledge proofs makes it challenging to run on mobile and low-power devices, and the ecosystem remains in its early stages.

Aztec: PrivacyPayment on Ethereum
Development Timeline: The Aztec project was launched in 2017, with its 2.0 version mainnet going live in 2021.
Core Features: By integrating zkSNARKand rollup technologies, Aztec batches multiple private transactions to generate a single unified proof, which is then submitted to the Ethereum mainnet. This approach ensures privacy protection while significantly reducing gas costs.
Applications and Ecosystem:Aztec Connect previously enabled users to conduct anonymous payments and yield farming operations on Ethereum, but the service was suspended in 2023.
Challenges: The trade-offs between privacy and regulation, as well as performance, persist, while the developer ecosystem requires further refinement.
Overall, the ZK (zero-knowledge) technology route offers high security and mathematical verifiability in privacy payments, making it particularly suitable for payment systems that require strong privacy protection and auditability. Its development trajectory demonstrates a gradual transition from academic prototypes to commercial applications, providing a technical foundation for subsequent Layer 2 privacy payments and complex smart contracts. Building on this foundation, BenFen’s privacy payment functionality further evolves the approach: by deeply integrating MPC protocols, zero-knowledge proofs, and the native privacy coin AUSD, it collaboratively generates private transactions off-chain. The system transforms core elements — such as input amounts, output amounts, sender/receiver addresses, and asset types—into cryptographic commitments or private states, using AUSD as the carrier for concealed assets, thereby ensuring that the flow of funds in transactions cannot be identified externally. Only the final validated state changes, verified via proofs, are synchronized on-chain. Nodes verify the correctness of these transformations without being able to reverse-engineer the original information, fundamentally blocking on-chain data analysis and achieving stronger protection for both asset and identity privacy.

Secure Multi-Party Computation (MPC)
Secure Multi-Party Computation (MPC) enables multiple participants to collaboratively compute a function and obtain results without disclosing their respective input data. It currently stands as one of the technologies closest to commercial application in the field of privacy payments. Unlike ZK (which often requires trusted setups) and TEE (which relies on specific hardware), MPC primarily ensures privacy through distributed algorithms and generally does not depend on complex pre-established trust assumptions. Representative projects include Partisia Blockchain and Lit Protocol.
Partisia Blockchain: A Foundation Public Chain Featuring MPC
Development Timeline: Partisia stands as one of the earliest projects to systematically integrate MPC technology into the foundational architecture of a blockchain.
Core Features: The project aims to build a foundational public chain with MPC as its core capability. By integrating threshold signatures (a practical application of MPC) and secret sharing technologies, it distributes transaction signing and complex computational tasks across multiple nodes, thereby preventing single-point privacy breaches. The system employs a hybrid MPC model algorithmically and leverages solutions like homomorphic encryption to optimize efficiency.
Applications and Ecosystem: Its MPC payment protocol has been piloted in scenarios such as decentralized advertising settlements, enabling verification and accounting without disclosing sensitive commercial data (e.g., specific transaction amounts). This design positions it as an ideal solution for cross-institutional data collaboration and enterprise-grade payment systems.
Challenges: The primary bottleneck of MPC lies in its substantial computational and communication overhead. The multi-party computation protocol requires frequent node interactions, resulting in high latency and strict network requirements. Although Partisia has optimized algorithmic efficiency, it still faces performance challenges in large-scale public chain environments demanding low latency.
Overall, the MPC approach represents a profound shift from institutional trust to algorithmic trust. It is not only used for payment signatures and settlement but has also expanded into areas such as identity verification, data sharing, and cross-border payments. To overcome performance bottlenecks, the industry is exploring “hybrid privacy architectures”, such as combining MPC with ZK proofs to compress verification steps, thereby accelerating the final confirmation process while ensuring privacy. BenFen has successfully broken through performance bottlenecks by adopting an MPC+ZK hybrid architecture, establishing itself as a next-generation public chain infrastructure that combines privacy protection with high-performance execution capabilities.
Compared to ZK’s “zero-knowledge proofs” and TEE’s “hardware black boxes,” the core advantage of MPC lies in its “decentralized collaboration.” It is particularly suited for privacy-preserving payment systems that require multi-party participation, complex account management, and compliance with audit requirements. As such, MPC plays the role of a “bridge connecting traditional finance with the crypto world” in the evolution of privacy payments, laying a solid foundation for subsequent technological solutions.
Modular and Cross-Chain Privacy Infrastructure
With the advancement of blockchain privacy technology, a trend toward modular and cross-chain privacy infrastructure has emerged. Modular privacy infrastructure abstracts privacy functions from single-chain or single-application implementations into reusable components, lowering the barrier to development and enabling developers to build privacy-focused applications more easily. For example, Aleo offers reusable privacy-smart contract modules to implement confidential transactions and privacy-preserving smart contract functionality. Cross-chain privacy initiatives aim to enable private asset transfers and partial contract interactions across different blockchains. For instance, Oasis’s Privacy Layer is designed to allow other chains or dApps to integrate privacy features (via bridging/messaging layers) and leverage the capabilities of its privacy-focused ParaTime. However, challenges remain due to protocol complexity and the need to enhance cross-chain security and standardization further.
This trend indicates that privacy is evolving from single-transaction protection to an infrastructure-level capability, enabling support for diverse scenarios such as DeFi, privacy payments, data transactions, and digital identity. However, modular and cross-chain privacy solutions still face challenges, including limited ecosystem scale, lack of standardization, cross-chain security risks, and interoperability constraints. Despite their significant technological potential, continuous refinement and validation are necessary before large-scale adoption can be achieved.
Technical Approach Comparison: How to Implement Privacy Payments?
Zero-knowledge proof
Zero-knowledge proofs are closely related to NP problems. Therefore, before proceeding to this module, allow me to introduce a mathematical challenge: the P vs. NP problem.
As the foremost of the seven Millennium Problems, P vs. NP is widely recognized. However, due to the simplicity of its formulation, most people do not grasp what P=NP truly signifies. P stands for Polynomial Time, which can be simply understood as problems that can be solved efficiently. NP stands for Nondeterministic Polynomial time, which can be simply understood as problems that can be verified efficiently. Therefore, the P vs. NP problem essentially asks: For a problem that can be verified efficiently, is there a hidden method to solve it efficiently? Are these two capabilities equivalent? If P=NP, it would mean that problems currently deemed intractable—such as combinatorial optimization in logistics scheduling—could be solved with surprisingly simple algorithms. Conversely, this would deal a fatal blow to cryptography based on large integer factorization and discrete logarithm problems, as hackers would inevitably discover fast algorithms to crack private keys or decrypt ciphertext. The prevailing view today is that P ≠ NP. This means we must accept that many world-class problems lack efficient algorithms. We must continually approximate solutions, forever unable to find the optimal one.
The traditional NP verification approach is remarkably simple, consisting of just two steps:
- Provide a Certificate: For an instance of an NP problem, if the answer is “yes,” there must exist a short, efficiently verifiable “proof” – this proof is the certificate.
- Run the verification algorithm: A deterministic algorithm exists that takes the problem instance and a candidate certificate as input. If the certificate is indeed a valid solution to the problem, the algorithm outputs “yes” in polynomial time; otherwise, it outputs “no.”
However, this verification approach has two significant drawbacks: privacy leakage of certificate information and the requirement for one-time passive acceptance of certificates.
To address these issues, zero-knowledge proofs emerged. The concept of zero-knowledge proofs was formally introduced and defined in the 1985 paper “The Knowledge Complexity of Interactive Proof Systems,” with its final version published in the Journal of the ACM in 1989. In this paper, authors Shafi Goldwasser, Silvio Micali, and Charles Rackoff (GMR) introduced two revolutionary concepts: interactive proof systems and knowledge complexity.
Traditional NP verification is static, one-time, passive, and deterministic. Interactive proofs, in contrast, are dynamic, multi-round, active, and probabilistic. Within this system, a Prover (P) interacts with a Verifier (V). V issues multiple random challenges to P, thereby achieving high probability assurance that P is correct. The logic is that if P’s statement is true, P can answer any question about it. If V receives accurate answers to all posed questions, V will conclude with high probability that P’s statement is correct. An interactive proof system must possess completeness and reliability: if a statement is true, an honest Prover can, through interaction, convince the Verifier with high probability; if the statement is false, any Prover has a negligible chance of convincing the Verifier after interaction.
In traditional proofs, focus is solely on validity and logical correctness. However, GMR raises a deeper question: When a verifier believes a statement is true, what additional knowledge—beyond this binary conclusion—does he gain? In other words, how much information does the proof process itself leak? Knowledge complexity is the metric introduced to quantify this information leakage. Notably, a knowledge complexity of zero signifies that the verifier gains no additional information beyond the statement’s accuracy—achieving zero-knowledge.
zk-SNARK Zero-Knowledge Succinct Non-Interactive Argument of Knowledge
The interactive proof systems introduced by GMR revolutionized the concept of proof, yet they suffer from inherent flaws: interactivity requires P and V to be constantly online, continuously exchanging information, and the proof process lacks reproducibility, making it unsuitable for effective large-scale broadcasting.
To address these shortcomings, Blum, Feldman, and Micali (BFM) proposed a conjecture: Could “interaction” be replaced with a method allowing the prover to independently generate a complete proof verifiable by anyone? They offered a solution: introducing a one-time, trusted setup phase. This setup phase generates a Common Reference String (CRS). The CRS is a random, publicly known bit string generated before any proof begins.
The BFM scheme operates as follows:
- Setup Phase: A trusted party randomly generates a CRS and makes it public. This step is performed only once.
- Proof Generation: When Prover P wishes to prove a statement, they no longer need to wait for the Verifier’s challenge. Instead, they use the CRS as a source of randomness to simulate challenges a verifier might pose. P independently computes a single, non-interactive proof using the CRS and their private information.
- Proof Verification: Upon receiving a proof w, any verifier V uses the same CRS to validate w’s validity. Since the CRS is public, anyone possessing it can act as a verifier.
Traditional verification of complex computations consumes substantial time and resources, which edge devices cannot afford. Therefore, the ideal verification state is one where the time and resources required for verification remain minimal and compact, regardless of the original computation’s complexity. In the 1990s, Probably Checkable Proofs (PCP) were introduced. Their core idea is that any mathematical proof verifiable in polynomial time (i.e., an NP problem) can be transformed into a special encoded form. The verifier need not examine the entire proof; by randomly sampling a very small number of bits from this encoded proof, they can determine the proof’s correctness with high probability. This theorem is extraordinarily powerful, demonstrating that a method exists where the verification effort is essentially independent of computational scale—precisely the goal pursued in verification simplicity. Although the introduction of PCP and BFM represented significant progress, they remained confined to the theoretical realm due to the technological limitations of the era and the lack of sufficiently mature cryptographic tools to integrate with them. Practical application remained distant.
In 2012, the first real-world implementation of zk-SNARKs was proposed: the Pinocchio protocol. This marked a groundbreaking breakthrough. The Pinocchio protocol provided an efficient compiler capable of converting C code into the circuits and parameters required for zk-SNARKs. It demonstrated for the first time that zk-SNARKs could be used to verify real-world computations. Although still slow, it transformed zk-SNARKs from a theoretical concept into a working prototype. Concurrently, another independent effort, GGPR, was introduced. The Quadratic Span Programs (QSP) and Quadratic Arithmetic Programs (QAP) proposed by Rosario Gennaro, Craig Gentry, Bryan Parno, and Mariana Raykova became the core technical foundation for most subsequent zk-SNARK systems.
Below is a separate introduction to these two works.
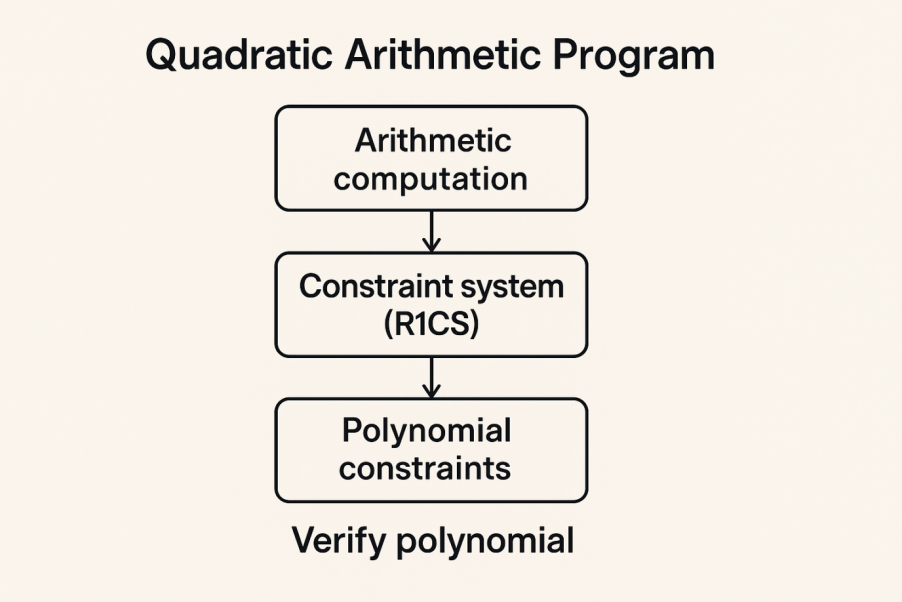
Both QSP and QAP aim to transform diverse computational problems into polynomial problems. However, as an improved version of QSP, QAP is more concise, standardized, and widely applicable. Therefore, we will focus solely on QAP. QAP operates under a strong assumption: any computational problem solvable by a deterministic Turing machine within finite computational resources can be transformed into an equivalent arithmetic circuit concerning polynomial divisibility problems. The core process of QAP is outlined below:
- Decompose any computation into the most fundamental addition and multiplication operations
- Construct a restricted linear constraint system (R1CS), establishing a set of quadratic constraints for each logical gate, namely
- Employ the Lagrange interpolation method to transform R1CS into a continuous constraint over a polynomial
- Verify the correctness of the polynomial
This transforms the proof of a computation problem into a polynomial problem. The prover only needs to demonstrate to the verifier that they know the final constructed polynomial to complete the proof.
The Pinocchio protocol was developed based on the theoretical foundation of QAP—a verifiable computation system that is almost practical. It optimised previous theoretical constructions and implemented the first high-performance, general-purpose zk-SNARK prototype system, thereby establishing the fundamental paradigm for modern zk-SNARKs. In October 2016, the Zcash cryptocurrency was launched. By utilising zk-SNARKs, Zcash is able to offer the dual capability of transparency, like Bitcoin, and privacy, concealing the sender, recipient, and transaction amount.
zk-STARK Zero-Knowledge Scalable Transparent Argument of Knowledge
Despite Zcash’s significant achievements, it also exposed several limitations of zk-SNARKs: requiring a trusted setup, poor scalability, and vulnerability to quantum computing. To address these challenges, in 2018, Eli Ben-Sasson et al. defined a novel zero-knowledge proof construction called zk-STARK (Zero-Knowledge Scalable Transparent Argument of Knowledge) in their paper “Scalable, Transparent, and Post-Quantum Secure Computational Integrity.” The three words in its full name correspond precisely to its three major innovations.
- Transparency – How to eliminate trusted setup?
Technical Core: Replacing trusted setup with a public random source (hash function)
- zk-SNARK’s Problem: Its security relies on structured public reference strings generated during trusted setup. If leaked by participants, these strings can be used to forge proofs.
- zk-STARK’s Solution:
- Completely abandon elliptic curve pairings and structured reference strings.
- Employ collision-resistant hash functions (e.g., SHA-256) as the sole cryptographic primitive.
- All public parameters (especially the “randomness” used for queries) are derived openly and reproducibly during proof generation through the verifier’s challenge and the hash function. No prior secret setup phase is required.
- Scalability – How to Achieve Logarithmic Verification Efficiency?
A. Algebraic Representation of Computation (AIR)
First, the paper introduces a method called Algebraic Intermediate Representation. It encodes computations requiring proof into a set of polynomial constraints. These constraints describe the mathematical relationships the program’s state must satisfy at each step of the computation.
B. Efficient Verification Using the FRI Protocol
This is the key to achieving “scalability.” The FRI protocol is used to prove that a function is indeed a “low-degree polynomial.” The entire process can be simplified into a multi-interaction “challenge-response” procedure.
- Knowledge Proofs – How is Security Guaranteed?
- Meaning of “Knowledge Proofs”: In cryptography, “proofs” typically refer to computationally sound proofs, where security relies on computational hardness assumptions. This contrasts with information-theoretically sound “proofs,” which offer unconditional security.
- Security Model of zk-STARK:
- Its security rests on the computational hardness assumption of hash function collision resistance.
- It constitutes a “knowledge” argument, meaning: if the prover genuinely possesses the required “evidence,” the verifier will accept the proof; if the prover lacks this knowledge, the probability of successfully forging a proof is extremely low.
That same year, Eli Ben-Sasson and others founded StarkWare to commercialize zk-STARK technology. They developed the new programming language Cairo and advanced two core products: StarkEx and StarkNet, issuing the STRK token. Following its Series D funding round in July 2022, StarkWare achieved a valuation of $8 billion.
Of course, zk-STARKs also have their own challenges. To achieve “transparency” (i.e., no trusted setup), zk-STARKs rely on cryptographic primitives like hash functions and Merkle trees. Their interactive proof process generates significantly larger data volumes, typically producing proof files in the hundreds of kilobytes range—much larger than zk-SNARK proofs (usually only a few hundred bytes). This significantly impacts on-chain transaction costs and transmission overhead. Furthermore, due to the complex mathematical operations involved in proof generation, the computational complexity is high. Generating a zk-STARK proof requires substantial computational resources, effectively raising the barrier to entry for users.
Additionally, it is important to note that both Zcash and StarkNet are built upon zero-knowledge proof (ZKP) technology. However, ZKPs only guarantee transaction privacy and do not provide robust solutions for managing private keys, asset allocation, or recovery procedures following unforeseen events. The inherent limitations of ZKPs necessitate the integration of complementary technologies to address these shortcomings. Fortunately, MPC offers a near-perfect solution that integrates with ZKPs at minimal cost. Therefore, combining with MPC is an essential path for ZKPs. We will further explore MPC concepts and present specific integration strategies in subsequent sections.
Mixers & Ring Signatures
In a nutshell, mixers anonymize assets by obscuring the origin of funds, while ring signatures anonymize transaction senders by obscuring the true signer. However, their implementation methods are fundamentally different.
Mixers
- Deposit (Commitment)
- The user generates a secret s and computes its hash: commitment = Hash(s).
- Funds are deposited into the contract along with the commitment. The contract publicly records the commitment.
- Waiting (Mixing)
- The user waits for other users to deposit funds, blending their transaction into a large “anonymous pool.”
- Withdrawal (Proof)
- The user wishes to withdraw funds to a new address.
- She generates a zero-knowledge proof to demonstrate to the contract: “I know the secret s corresponding to one of the commitments in the list, and no double-spending has occurred.”
- Simultaneously, she publicly discloses nullifier = Hash(s) (matching the deposit receipt) to prevent double-spending.
- Verification and Disbursement
- The contract validates the zero-knowledge proof and checks if the nullifier remains unused.
- Upon successful verification, the contract transfers funds to the user’s specified new address and marks the nullifier as spent.
Ring Signatures
To address anonymity leakage, Ronald Rivest, Adi Shamir, and Yael Tauman jointly proposed the concept of ring signatures in 2001. Over the following years, it rapidly evolved into multiple variants for diverse applications, such as linkable ring signatures, threshold ring signatures, and traceable ring signatures. Linkable ring signatures prevent the same private key from signing multiple times within the ring, primarily used to prevent double-spending in cryptocurrencies like Monero. Traceable ring signatures can reveal the signer under specific conditions, mainly employed in anonymous systems requiring accountability. Threshold ring signatures require multiple parties to collaborate to generate a signature, primarily used in scenarios like anonymous collaborative authorization. Fundamental ring signatures can be broadly categorized into two types based on implementation: RSA-based and elliptic curve-based.

Below is a typical elliptic curve ring signature scheme (SAG paradigm).
- Key Image
The actual signer (indexed as ( s )) computes the key image ( I ) using their private key ( x_s ):
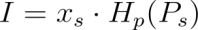
where (H_p(\cdot)) is a hash function mapping inputs to points on the elliptic curve.
- Initialization and Challenge Chain Initiation
The signer selects a random seed (α) and computes the initial commitment:
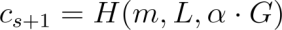
where (H) is a hash function with scalar output, and (G) is the generator of the elliptic curve.
- Generating Responses for Other Members (Simulation)
For all positions (i ≠ s) (i.e., non-authentic signers), the signer randomly generates (r_i) and computes:
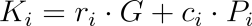
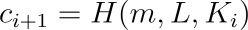
- Generating Responses for the Actual Signer (Closing the Loop)
At the actual signer’s own position (s), they compute the response (r_s) using their private key (x_s) to close the loop:
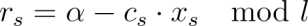
where (l) is the order of the elliptic curve group.
- Verification Process
The verifier uses the sequence (c₁) and (r_i) from the signature to recalculate for all (i = 1) to (n):
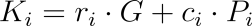
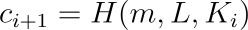
Finally, verify whether the ring closes, i.e., check if the following equation holds:
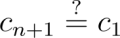
If the equation holds and the key image (I) has not been used, the signature is valid.
Specific Implementation
The most renowned representative of coin mixers is Tornado Cash, while Monero stands out as the most prominent example of ring signatures. Both offer robust anonymity, but precisely because of this, regulatory bodies in some countries have required cryptocurrency exchanges to delist Monero, as it struggles to comply with anti-money laundering regulations. In 2022, the U.S. Treasury Department’s Office of Foreign Assets Control (OFAC) sanctioned Tornado Cash’s smart contract addresses, citing its use in laundering hundreds of millions of dollars in hacked funds. Subsequently, its GitHub repository was seized, and its developers were arrested. Thus, while mixers and ring signatures are powerful, their untraceable nature subjects them to significant regulatory pressure and legal risks.
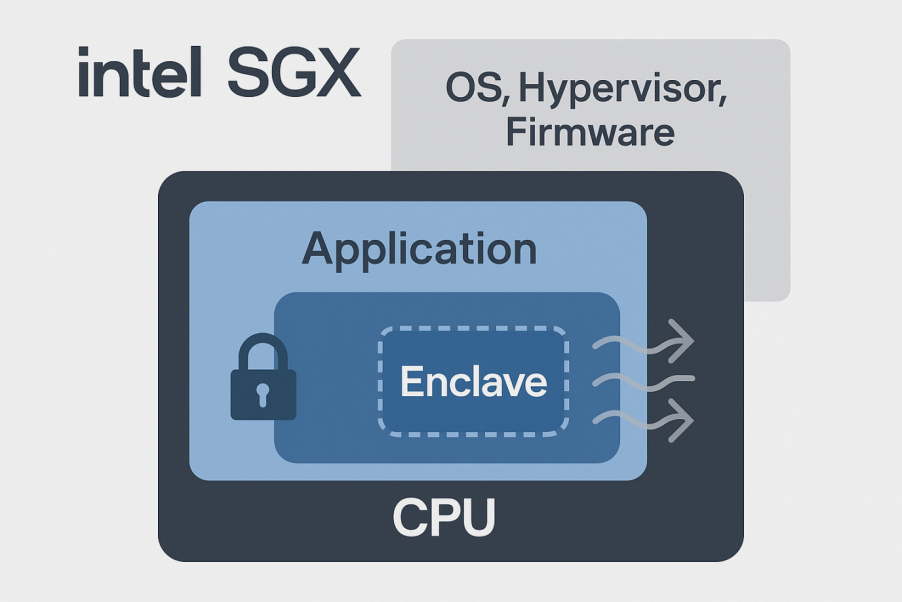
Trusted Execution Environment (TEE, Intel SGX)
Trusted Execution Environment (TEE) is a core technology designed to safeguard the secure operation of sensitive programs within computing devices. Its fundamental principle involves strictly isolating hardware and software to provide sensitive programs with a secure execution environment completely separated from the general-purpose computing environment. TEE technology was developed to address the fundamental security issue in traditional computing models where the operating system or virtual machine monitor, as the highest-privileged entity, could become a potential attack surface. BenFen Chain adapts the hardware isolation concept of TEE for privacy payments. By off-chain MPC (Multi-Party Computation) to collaboratively generate encrypted transactions, it only records state changes on-chain. This achieves similar isolation and protection of sensitive data, preventing direct on-chain exposure.
The core objectives of TEE are to ensure data confidentiality, integrity, and the trustworthiness of computational processes. By leveraging built-in processor hardware security features, TEEs ensure data remains encrypted in memory during code execution, with decryption and processing confined solely within the TEE. This hardware-assisted isolation fundamentally distinguishes TEEs from pure software sandbox environments, providing a more robust root of trust.
The core value of TEEs lies in establishing hardware-assisted trust boundaries. Traditional software isolation mechanisms rely on the integrity of the operating system. Once the OS kernel is compromised, all application data and code running on it become exposed. However, by partitioning the CPU into a “Secure World” and a “Non-Secure World,” the TEE enables security-sensitive programs to operate within the Secure World. Even if the OS or Hypervisor in the Normal World is completely compromised, it cannot directly access or tamper with data or execution processes within the Secure World.

The implementation of this isolation mechanism typically involves specialized memory management units, memory encryption engines, and specific CPU instruction sets. For example, Intel SGX ensures data within the Enclave remains encrypted after leaving the CPU boundary by encrypting the page cache. This design significantly reduces the system’s overall attack surface by narrowing the trust boundary to the Enclave itself. Below is an analysis of mainstream TEE architectures:
ARM TrustZone (TZ) Architecture Analysis
ARM TrustZone is the most widely deployed TEE technology in mobile and embedded devices. Based on hardware partitioning principles, it divides the SoC’s hardware and software resources into two independent execution environments: the Secure World and the Normal World.
Core Principle: Hardware-level isolation is controlled by specific mode bits within the CPU. During system boot, the Secure World is entered first, where a secure operating system manages the TEE environment. Switching between the two worlds is managed by the secure monitor using specific SMC instructions.
Isolation Mechanism and Challenges: TrustZone’s isolation granularity operates at the operating system level. This means security-sensitive applications run atop a complete secure operating system kernel. While this provides rich functionality, its security model relies on the integrity and vulnerability immunity of the secure OS itself. The secure OS’s code base is significantly larger than Intel SGX’s micro-enclave, resulting in a relatively larger attack surface that requires ongoing auditing and maintenance.
Intel Software Guard Extensions (SGX) Architecture Analysis
Intel SGX is a fine-grained TEE technology designed for data center and desktop platforms. It reduces protection granularity to the application level, enabling developers to encapsulate sensitive code and data within a protected memory region called an Enclave.
Core Principle: SGX achieves isolation through a specialized instruction set and memory encryption mechanisms (EPC). Data within the EPC is encrypted by the memory encryption engine before leaving the CPU chip, preventing snooping by the OS, hypervisor, or even motherboard firmware.
Isolation Mechanism and Challenges: SGX’s greatest strength lies in its minimal root of trust. Code within the Enclave is the only trusted software. However, this deep integration into complex microarchitectures makes SGX a prime target for side-channel attacks. For instance, SGX utilizes caching and paging mechanisms, where these shared resources become ideal channels for attackers to exploit timing differences for information extraction. Its remote attestation mechanism is also relatively complex, requiring reliance on Intel’s signature service to verify the Enclave’s authenticity and integrity.
Although TEEs provide robust security through hardware isolation, their trust model is not flawless. Early TEE architectures focused on providing isolation mechanisms for memory and execution logic to resist direct snooping and tampering from high-privilege software environments. However, with advances in processor technology and increasingly complex microarchitectures, research has revealed that the TEE’s “isolation-only” nature renders it vulnerable to “software-based side-channel attacks” exploiting microarchitectural state leaks. Modern CPUs, in pursuit of extreme performance, extensively utilize shared resources. These shared resources inadvertently create communication channels between the secure and non-secure worlds. When sensitive programs execute within the TEE, their memory access patterns cause measurable changes in the state of shared hardware resources. Attackers operating in the non-secure world can infer confidential information being processed inside the TEE—such as cryptographic keys or execution paths of sensitive algorithms—by measuring these changes in microarchitectural states.
Several major TEE security vulnerabilities and attacks have occurred historically. Below are brief introductions to two notable examples:
- Foreshadow (L1TF) – Targeting Intel SGX
- Timeline: Disclosed in 2018
- Core Vulnerability: A flaw in Intel CPUs’ speculative execution mechanism, specifically the L1 cache stalling.
- Attack Mechanism: Exploits the CPU’s speculative execution vulnerability to trick the CPU into loading protected data from enclaves into the shared L1 cache before a fault occurs. Attackers can then detect this data via cache side-channel attacks, stealing enclave secrets like keys and passwords.
- Severity: Extremely high. It breaks SGX’s core security promise by extracting arbitrary data from enclaves. Variants targeting operating system kernels and virtual machine monitors also exist.
- AEPIC Leap – Targeting Intel SGX
- Timeline: Disclosed in 2022
- Core Vulnerability: An extremely rare architectural flaw. A design defect in the CPU’s memory-mapped I/O allows unmapped memory contents to potentially leak through the CPU’s prefetcher.
- Attack Mechanism: Attackers can construct specific MMIO accesses causing the CPU prefetcher to load enclave private data into cache, enabling extraction via side channels. Its uniqueness lies in being an architecture-verifiable vulnerability that doesn’t rely on timing measurements from side-channel analysis, theoretically offering higher reliability and precision.
- Severity: Extremely high. This demonstrates that even flawless microarchitectural implementation can be undermined by architectural oversights, leading to catastrophic data exposure.
Consequently, the greatest challenge for TEE technology lies not in achieving logical isolation, but in addressing the physical/timing-based shared channels introduced by CPU performance optimizations. This challenge compels security research to shift from purely isolation-based defenses toward complex runtime integrity proofs and side-channel immunity designs.
Fully Homomorphic Encryption (FHE)
Fully Homomorphic Encryption (FHE) is an effective method for addressing privacy and security challenges. It is a powerful encryption tool whose core capability lies in enabling arbitrary homomorphic computations on encrypted data. This means that, in theory, any complex algorithm or computational circuit can be executed directly on ciphertexts without prior decryption. The BenFen Chain adopts a hybrid FHE-MPC (Multi-Party Computation) model that performs encrypted-state computation at the underlying layer, ensuring that data remains encrypted throughout the process, which aligns perfectly with the core concept of FHE.
The development history of fully homomorphic encryption is a continuous optimization process from theoretical breakthrough to engineering practice. It began with the first feasible solution proposed by Gentry in 2009, but this solution was only of theoretical significance due to extremely low computational efficiency. Subsequently, the research focus quickly shifted to the second and third generation schemes based on lattice-based hard problems, especially those relying on Learning with Errors (LWE) and Ring Learning with Errors (RLWE).
Definition of Homomorphic Encryption (HE) and Fully Homomorphic Encryption (FHE)
An encryption scheme E is called homomorphic encryption (HE) if it supports homomorphism for a specific operation ∘ . Formally, if E (m1) ∘ E (m2)=E (m1 ∘ m2), then the scheme is said to be homomorphic.
Fully Homomorphic Encryption (FHE) is a more powerful structure. It requires that the encryption scheme support both fundamental homomorphic operations. In Boolean circuits, addition and multiplication are sufficient to construct any complex computational function, thereby enabling any homomorphic computation on the encrypted data. This capability renders FHE Turing-complete in terms of computation.

The Predecessor of FHE: Partially Homomorphic Encryption (PHE)
Before the emergence of Fully Homomorphic Encryption (FHE), the cryptography community had already developed encryption schemes supporting a single type of operation, known as Partially Homomorphic Encryption (PHE).
RSA Algorithm: RSA, one of the cornerstones of public-key cryptography, possesses multiplicative homomorphism. Specifically, for ciphertexts E (m1) and E (m2), their product, after decryption in the ciphertext space, equals the modulo N result of the plaintext product: E (m1) ⋅ E (m2) = E (m1 ⋅ m2 (modN) ). However, RSA cannot perform addition operations on ciphertexts.
Paillier Algorithm: The Paillier algorithm is another widely used PHE scheme that supports additive homomorphism. In this scheme, the multiplication operation in the ciphertext space corresponds to the addition operation in the plaintext space: E (m1) ⋅ E (m2) = E (m1 + m2 (modN) ). Paillier is highly effective in applications such as secure voting systems, but it cannot perform multiplication operations on ciphertext.
Key Obstacle: The Leap from Partial to Full Homomorphism
The limitation of PHE schemes is their inability to support general-purpose computation. A computational circuit requires both AND and XOR functionality to implement arbitrary logic. RSA and Paillier only provide one of these, severely restricting their applicability. Moreover, because PHE schemes typically support only a limited number of operations or a single operation, they do not need to handle noise accumulation problems during ciphertext operations in their design.
The transition from PHE to FHE is not merely about adding an operation — it crosses the threshold to Turing completeness. Once it is required to support arbitrary-depth, mixed addition and multiplication operations, the noise introduced by the encryption scheme to maintain security will become a fatal flaw. This demand for complexity makes the noise management mechanism an indispensable core component in FHE architecture.
In 2009, Craig Gentry successfully constructed the first feasible FHE scheme based on hard problems in ideal lattices. This milestone marked the transition of FHE from theoretical fantasy to practical possibility.
Gentry not only provided a concrete scheme but also proposed a general theoretical framework for constructing FHE. The core idea of this framework is to decompose the construction of FHE into two steps: first, build a scheme that supports a Somewhat Homomorphic Encryption (SHE), and then use a bootstrapping mechanism to elevate the SHE scheme into a fully homomorphic scheme capable of supporting unlimited homomorphic operations.
In lattice-based encryption schemes, to achieve semantic security (i.e., the same plaintext can encrypt to different ciphertexts), random errors or noise must be introduced during encryption. The existence of noise is the foundation of the security of the FHE scheme, but it is also the greatest obstacle to the functionality of the FHE scheme. As homomorphic operations, especially homomorphic multiplication, are continuously performed, the noise in the ciphertext will accumulate and increase. Once the size of the noise exceeds the threshold set by the scheme parameters, the decryption process will be unable to correctly restore the original plaintext, thereby causing decryption errors. Therefore, an operation must be designed to effectively reduce the noise in the ciphertext to ensure the correctness of the computation.
Bootstrapping is the core technique in Gentry’s framework for addressing noise accumulation. It is defined as: when the noise in a ciphertext approaches the threshold and further computation would be impossible, the ciphertext undergoes a homomorphic decryption of itself. In this process, the private key itself is encrypted. The result is a new ciphertext encrypting the same plaintext but with significantly reduced noise, allowing further homomorphic operations. Bootstrapping is currently regarded as the only viable approach to achieving FHE and is a key component of any FHE scheme.
Gentry’s scheme, representing the first generation of FHE, faced the challenge of enabling an SHE scheme with limited computational depth to homomorphically evaluate its own decryption circuit. By leveraging sparse subsets and careful assumptions, Gentry preprocessed complex operations within the decryption circuit, successfully compressing it so that the decryption could be performed within the supported homomorphic depth, achieving bootstrapping.
However, the first-generation FHE came at a tremendous computational cost. Using Boolean circuits to encrypt key information bit by bit, bootstrapping a single bit took approximately 30 minutes. This enormous overhead meant Gentry’s scheme was a theoretical feasibility proof rather than a practical technology. The high computational cost remains the primary performance bottleneck for the industrial application of FHE.

Transition to Lattice-Based Hard Problems: LWE and RLWE
To overcome the inefficiency and complex Boolean circuit structure of Gentry’s first-generation scheme based on ideal lattices, researchers began seeking more efficient algebraic structures and more manageable noise models. Second-generation FHE schemes shifted to using the Learning With Errors (LWE) problem and its ring variant, the Ring Learning With Errors (RLWE) problem, as their security foundations.
This shift represented a pivotal engineering decision in the evolution of FHE. The algebraic structure provided by LWE/RLWE allows for more effective noise management—particularly RLWE, which transforms complex matrix operations into faster polynomial computations, thereby laying the groundwork for subsequent optimizations. The BGV (Brakerski-Gentry-Vaikuntanathan) and BFV (Brakerski/Fan-Vercauteren) schemes are representative examples of this generation.
BGV and BFV: Levelled Homomorphic Encryption and Noise Management
Second-generation schemes introduced the concept of Levelled Homomorphic Encryption (LHE). In an LHE scheme, parameters are configured in advance to determine the maximum number of supported homomorphic multiplications—that is, the circuit depth.
The BGV scheme is one of the first compact FHE constructions based on LWE/RLWE. It introduced a dynamic noise management technique known as modulus switching. Rather than relying entirely on the computationally expensive bootstrapping operation, modulus switching reduces the ciphertext modulus after each homomorphic multiplication, proportionally decreasing the relative size of the noise to the modulus. This effectively “buys” additional computational levels. Only when all preset levels are exhausted and deeper computation is required does the scheme need to perform a full bootstrapping operation.
The BFV scheme is primarily designed for exact integer arithmetic. Its optimizations focus on reducing initial noise and improving the efficiency of modulus switching. For instance, initial noise can be reduced by precomputing transformations such as ⌊tq⌋m→⌊tqm⌋. Another important optimization is performing modulus switching after the relinearization operation, thereby lowering the dimensionality required for modulus switching. Additionally, by structuring the modulus in layers and switching to smaller moduli after multiplications, BFV can further slow the rate of noise growth.
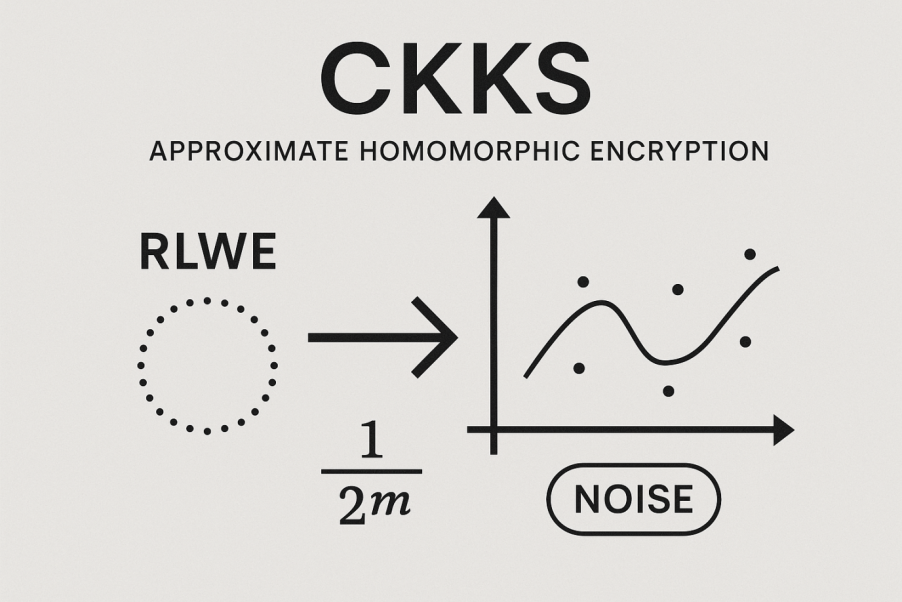
CKKS Scheme (Cheon–Kim–Kim–Song): Approximate Homomorphic Encryption
The CKKS scheme is specifically designed for performing homomorphic computations over real and complex numbers. It supports approximate arithmetic, which is essential for applications in statistical analysis, machine learning, and artificial intelligence.
Core Assumption: CKKS is built upon the algebraic structure of the Ring Learning With Errors (RLWE) problem, which naturally enables SIMD (Single Instruction, Multiple Data) parallel operations.
Noise Handling and Precision: CKKS is designed to tolerate controlled approximation errors, which are used to encode the precision of floating-point numbers. Therefore, the primary focus of CKKS optimization lies in improving computational accuracy after bootstrapping. Researchers achieve precise modulus reduction through various approximation functions. Depending on the implementation approach, the bootstrapping precision of CKKS-based schemes varies widely—from approximately 24 bits in early versions to as high as 255 bits in the most advanced designs today.
FHE offers unique advantages in addressing modern data privacy challenges:
Data Sovereignty and Privacy Protection: The core value of Fully Homomorphic Encryption (FHE) lies in its ability to perform computations on sensitive data in untrusted environments without exposing the data content to service providers. This greatly enhances data privacy protection and enables the separation of data ownership and data usage rights, ensuring users maintain full control over their information.
Support for Arbitrary Computation: By supporting both addition and multiplication as fundamental operations, FHE achieves Turing-complete computational capability over encrypted data. This allows FHE to be applied to complex tasks such as machine learning model evaluation, genomic data analysis, and financial modeling, use cases that are far beyond the capabilities of partially homomorphic encryption (PHE) schemes.
Theoretical Post-Quantum Security: Modern FHE schemes, based on Learning With Errors (LWE) and Ring Learning With Errors (RLWE), rely on lattice-based hard problems that are widely believed to be resistant to quantum attacks. This gives FHE a long-term security advantage over traditional public-key cryptosystems such as RSA and ECC.
High Throughput via SIMD Parallelism: Schemes built on RLWE structures (such as BGV and CKKS) employ SIMD (Single Instruction, Multiple Data) techniques through ciphertext packing, allowing multiple data elements to be processed in parallel. This significantly offsets the high computational cost of individual homomorphic operations, thereby improving throughput in practical applications.
Although FHE has made remarkable progress, its industrial application still faces multiple challenges:
Computational Performance Bottleneck: Although bootstrapping time has been reduced dramatically—from about 30 minutes in Gentry’s original scheme to the millisecond scale today—homomorphic operations still remain several orders of magnitude slower than their plaintext equivalents. The high computational cost of bootstrapping remains the primary performance bottleneck in FHE implementations.
Ciphertext Expansion and Storage Overhead: FHE ciphertexts are typically much larger than the original plaintexts. This ciphertext expansion leads to significant storage and bandwidth overhead, increasing system complexity and operational costs. For instance, LWE/RLWE ciphertexts must use multiple high-dimensional polynomials to represent a single plaintext message in order to manage noise and support relinearization.
Complex Key Management: FHE requires managing large and intricate key structures, especially evaluation keys used for relinearization and bootstrapping. These keys can be very large in size and complex to distribute or maintain, posing additional challenges for secure deployment and system scalability.
Secure Multi-Party Computation (MPC)
Core Paradigm and Mathematical Definition of MPC
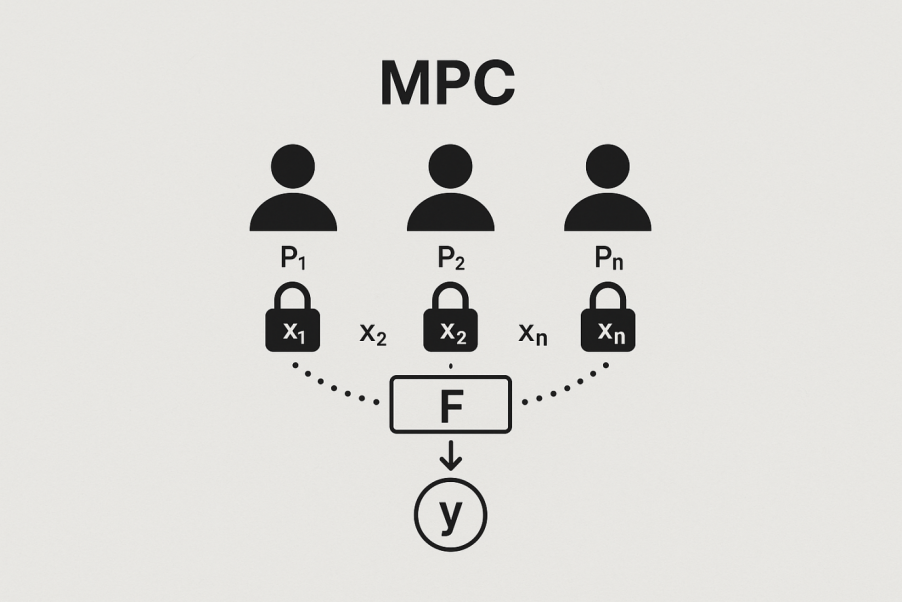
Secure Multi-Party Computation (MPC) is one of the fundamental areas of research in modern cryptography. Its primary goal is to resolve the inherent conflict between data privacy and collaborative computation. MPC enables n mutually untrusted participants, denoted as P1,…, Pn, to jointly compute a predefined function F (x1, …, xn) = y without revealing their private inputs x1, …, xn to one another. This paradigm achieves secure computation by decomposing the target function into basic operations that can be securely executed on encrypted or shared data.
The security of MPC is defined primarily by two core properties: input privacy and output correctness. Input privacy requires that no participant or external adversary should be able to learn anything about the private inputs of other parties from the execution of the protocol, except for what is inherently revealed by the final output. The correctness of the result ensures that the output y must be exactly equal to the result of evaluating F on all participants’ inputs. Furthermore, the protocol must ensure that even if some participants behave maliciously, they cannot alter or bias the correctness of the computed output. Depending on the underlying cryptographic primitives, MPC protocols are generally divided into two major categories: Garbled Circuit (GC)-based protocols and Secret Sharing (SS)-based protocols
Phased Development and Historical Milestones of MPC
The development of MPC has not been linear; rather, it has undergone a transformation from an abstract mathematical concept to a practical engineering system. This report divides the evolution of MPC into several key stages, aiming to precisely analyze the construction of its theoretical foundations, the advancement of security standards, the breakthroughs in engineering efficiency, and its final industrial adoption:
- Theoretical Foundation and Feasibility Proof: Establishment of the two fundamental protocol paradigms of MPC.
- Theoretical Deepening and Model Expansion: Introduction of system-level security frameworks.
- Efficiency Breakthrough and Transition Beyond Theory: Through algebraic optimizations and hybrid protocols, MPC evolved from an academic prototype to an engineeringly feasible system.
The BenFen Privacy Payment System exemplifies the industrial realization of these evolutionary stages. Its FAST MPC module in the initial version implements secure transaction generation and verification entirely through MPC. In future iterations, the system plans to integrate MPC with FHE-based architectures, enabling more complex functionalities — such as advanced cryptographic fusion frameworks that support sub-second privacy confirmation and a zero-gas-feeuser experience.
Theoretical Foundations and Feasibility Proofs
The 1980s marked the theoretical beginning of Secure Multi-Party Computation (MPC). The key contribution of this era was the formal proof that general secure computation is feasible, along with the establishment of two fundamental protocol paradigms.
Yao’s Garbled Circuits (GC)
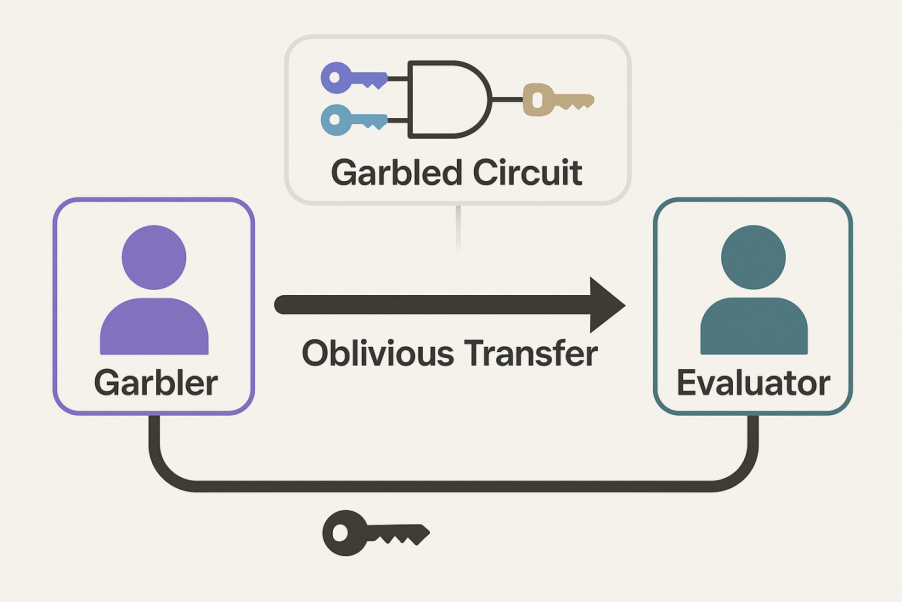
Yao’s Garbled Circuit (GC) protocol stands as one of the most iconic techniques in the field of secure computation. While the conceptual origin can be traced back to Andrew Yao’s 1982 “Millionaires’ Problem”, the full protocol and its practical implementation details were developed in subsequent research. The GC protocol introduced the first two-party secure computation framework, allowing two mutually untrusted parties to jointly evaluate a function without the need for a trusted third party.
The mechanism of GC requires transforming an arbitrary function into a Boolean circuit. The protocol involves two main roles: the Garbler and the Evaluator. The Garbler constructs a garbled circuit by replacing each gate’s truth table with encrypted values derived from random encryption keys. The Evaluator obtains the corresponding input key labels through an Oblivious Transfer (OT) protocol, ensuring that neither party learns the other’s private input. Using these encrypted labels, the Evaluator can then securely evaluate the garbled circuit to obtain the encrypted output. A key advantage of the GC protocol lies in its constant-round communication property — the number of communication rounds remains fixed regardless of the depth or size of the Boolean circuit. This feature is crucial for low-latency applications deployed over wide-area networks, as it effectively avoids the high overhead associated with network delays. However, the original GC protocol is inherently suited for two-party computation; extending it to multi-party settings requires introducing additional and complex mechanisms.
GMW Protocol and BGW Protocol
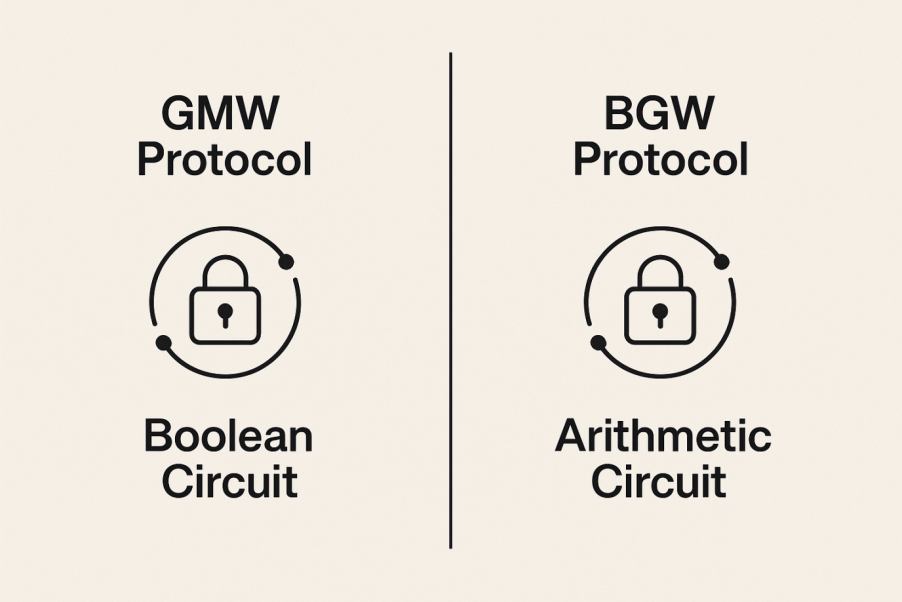
Unlike the GC-based path to secure computation, in 1987, Goldreich, Micali, and Wigderson proposed the GMW protocol, which provided a path to general multi-party computation based on secret sharing and information-theoretic security.
The GMW protocol operates on Boolean circuits, and its main mechanism relies on secretly sharing the input among all participants. Under the GMW protocol, if the number of corrupted parties t satisfies the honest majority condition, the protocol can achieve unconditional security, that is, information-theoretic security, without relying on any computational complexity assumptions. This means that even if an attacker possesses unlimited computational power, they cannot learn any information about the secret inputs from the shared data.
Alongside it is the BGW protocol (Ben-Or–Goldwasser–Wigderson), which is also based on secret sharing but is mainly applied to arithmetic circuits rather than Boolean circuits. Unlike the GC protocol, the communication rounds of the GMW and BGW protocols usually depend on the depth of the circuit corresponding to the function being computed. This characteristic makes their performance often inferior to the constant-round GC protocol in high-latency network environments.
The theoretical foundation phase of MPC established two independent security paradigms. The GC protocol provides a constant-round, computationally secure solution, focusing on low-latency optimization; while the GMW/BGW protocols offer information-theoretically secure solutions that depend on circuit depth, focusing on multi-party robustness. This divergence is theoretically necessary, as it reveals the inherent contradiction between achieving constant-round communication and multi-party information-theoretic security without compromising computational assumptions.
Although secret sharing itself is not a complete MPC protocol, it serves as a fundamental toolbox for multi-party protocols such as GMW and BGW, enabling secure function evaluation and resistance to malicious behavior. However, at this stage, MPC faced a major challenge — the lack of a universal protocol capable of simultaneously achieving high efficiency, multi-party support, information-theoretic security, and constant-round communication. The initial implementations of MPC suffered from huge communication overhead and complexity, which limited their applicability in real-world scenarios.
Theoretical Deepening and Model Expansion
After the feasibility of MPC was established, the focus of research shifted to how to define and ensure the security of protocols in complex, dynamic, and composable environments.
Universal Composability (UC) Framework
Around 2001, Ran Canetti proposed the Universal Composability (UC) framework, aiming to address the limitations of traditional cryptographic models in defining protocol security. Traditional security definitions often focus only on a protocol’s stand-alone security, while neglecting potential vulnerabilities that may arise when a protocol is used in parallel or nested with other protocols.
The core idea of the UC framework is to define protocol security as its equivalence to an “ideal functionality.” An ideal functionality is a theoretical, perfectly secure entity that flawlessly performs the intended computation and guarantees complete security. If a real-world protocol P is indistinguishable from the ideal functionality F in any environment, then P is said to be UC-secure. The UC framework models protocols using interactive Turing machines, which activate one another by reading and writing to communication tapes, thereby simulating communication and computation within a network.
The introduction of the UC framework greatly raised the standards for cryptographic protocol design and became the common language for modern cryptographic security analysis. However, the UC framework also quickly revealed theoretical limitations. Research within the UC model showed that achieving UC-secure multi-party computation in the “plain model” is impossible. This impossibility result forced researchers to turn to non-plain models, such as those relying on non-malleable commitments or other forms of public setup assumptions. This means that, to achieve security in complex system-level environments, MPC protocols must rely on certain pre-established infrastructures, rather than being completely standalone. In addition, the UC framework’s explicit modeling of asynchronous communication and network delay—for example, revealing potential information leakage through delay mechanisms—also indirectly promoted the continuous optimization of constant-round protocols to improve their tolerance to network variability.
Efficiency Breakthroughs and Moving Beyond Pure Theory
In the mid-to-late 2000s, MPC experienced a critical turning point, as a series of algorithmic and engineering improvements transformed it from an academic concept into an engineering-feasible system.
Early Implementations of General MPC Systems: Fairplay (2004)
Fairplay was the first notable implementation of a general secure computation system, introduced by Malkhi et al. in 2004. The emergence of Fairplay marked the first large-scale transition of MPC research from theoretical papers to engineering practice.
The Fairplay system included a high-level process definition language (SFDL), a compiler that translated SFDL into SHDL, and Alice/Bob programs that executed Yao’s protocol. The main security guarantee of this system was that its computation result was equivalent to that of a designated trusted third party—ensuring both the correctness of the computation result and that no information beyond what is implied by the output would be revealed about the inputs.
The implementation of Fairplay was crucial. Not only did it validate the theoretical feasibility of MPC, but more importantly, it exposed significant performance bottlenecks in real-world applications, especially in circuit compilation and communication overhead. This engineering practice provided feedback to theoretical research, directly motivating the optimization of underlying cryptographic primitives and circuit structures.
Advanced Optimization Techniques for Garbled Circuits
Although GC (Garbled Circuits) had the advantage of constant-round communication, its communication overhead grew proportionally with circuit size, becoming the main obstacle to early practical adoption.
Free-XOR Technique
The Free-XOR technique, introduced by Kolesnikov and Schneider, is one of the most important milestones in the history of GC efficiency. By cleverly designing the key-label structure, this technique allows XOR gates to be evaluated completely for free, i.e., without any additional encryption operations or communication costs. This dramatically reduced the bandwidth and computational burden of Boolean circuits, particularly for functions containing many addition or XOR operations, such as memory access and partial hash computations. The optimization effect of Free-XOR was significant and was later extended to multi-party protocols, such as the BMR protocol. Furthermore, through the introduction of Half-Gates and other optimizations, the encryption operations required for each AND gate were reduced to only two ciphertexts, achieving further compression and acceleration of GC.
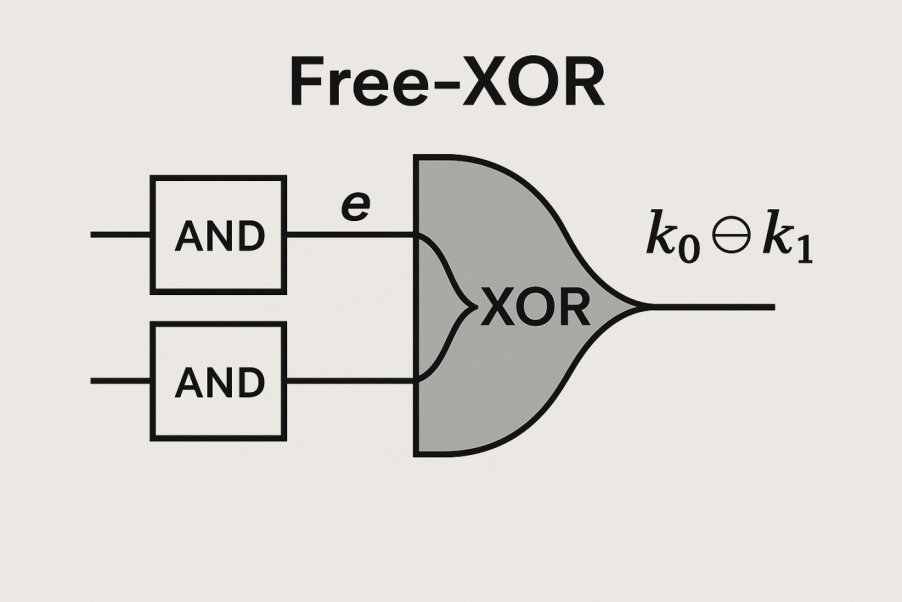
Cut-and-Choose Optimization under the Malicious Model
Under the malicious security model, although the Cut-and-Choose technique is effective, it also introduces significant computational cost. Research efforts have focused on optimizing the parameter selection of Cut-and-Choose. By formalizing the Cut-and-Choose game as a constrained optimization problem and considering the difference between checking cost and evaluation cost, researchers were able to design more efficient strategies, thereby improving bandwidth efficiency by an order of magnitude and achieving a 12% to 106% improvement in total execution efficiency under the malicious model.
The Emergence of Hybrid Protocols and Efficient Preprocessing
Recognizing the limitations of pure GC and pure secret-sharing-based protocols, researchers began to design hybrid protocols that combine the strengths of both approaches.
Integration of Somewhat Homomorphic Encryption
The core of hybrid protocols lies in leveraging the properties of Somewhat Homomorphic Encryption (SHE) or Fully Homomorphic Encryption (FHE). SHE allows linear operations on ciphertexts (such as homomorphic addition). This integration enables the protocol to adopt a separated architecture of the Offline/Online phase.
In the offline phase, participants use SHE or related cryptographic primitives, such as Oblivious Transfer (OT), to generate the necessary cryptographic material, such as Beaver triples or OLE-related randomness. This offline phase is typically computationally intensive but non-interactive, and independent of the actual inputs.
In the online phase, once private inputs arrive, the protocol only involves efficient share exchanges and verification of information-theoretic MACs, without any expensive cryptographic operations. This architecture shifts the computational burden and network-latency sensitivity to the offline phase, making the online phase, which is more critical to user experience, extremely efficient.
The development of Secure Multi-Party Computation (MPC) is a history of evolution from purely mathematical feasibility proofs to highly efficient engineering implementations. Starting from the theoretical foundations in the 1980s, MPC established two main branches: constant-round, computationally secure GC-based protocols and circuit-depth-dependent, information-theoretically secure GMW/BGW-based protocols. Subsequently, the introduction of the UC framework raised security standards and revealed the infrastructure requirements necessary to achieve security in complex environments.
In the mid-to-late 2000s, the engineering practice exemplified by Fairplay exposed bottlenecks that directly drove algebraic optimizations such as Free-XOR and Half-Gates, as well as hybrid protocol architectures driven by SHE/OLE. These techniques improved the efficiency of MPC by several orders of magnitude, enabling practical commercial deployment and even achieving efficiency close to insecure computation under the malicious security model.
Why We Choose MPC
The Combination of MPC and Privacy Payment
Application of MPC in Decentralized Key Management
Multi-Party Custody and Mnemonic-Free Recovery
The core application of MPC in key management is the Threshold Signature Scheme (TSS). TSS allows N participants to collaboratively generate a valid digital signature without reconstructing the private key in plaintext (S). As long as T shares are collected, a signature can be produced. This ensures that the private key S never exists in plaintext on any single device or with any single entity.
MPC wallets leverage this property to address two major challenges in traditional cryptocurrency storage: loss of mnemonic phrases and private key leakage risks. By distributing key shares and implementing a threshold mechanism, MPC provides a native multi-authorization framework.
BenFen is particularly notable in this field. Its MPC-based TSS splits the private key into multiple encrypted shares and distributes them across different nodes, ensuring that the private key never appears in plaintext. The mnemonic-free recovery mechanism allows users to recover assets through multi-party collaboration without relying on traditional mnemonic backups, significantly reducing the risk of asset loss or theft due to lost or compromised mnemonics. Furthermore, BenFen’s TSS architecture supports dynamic participant management, allowing the signature threshold to be adjusted flexibly without compromising security, thereby accommodating the needs of both institutional and individual users.
Institution-Level Security and Compliance
For institutional finance, MPC provides a highly robust security framework. The signing of any large-value transaction requires a predefined multi-party consensus, ensuring the safety of funds. Moreover, the robustness of MPC derives from its (t, n) security model: even if t participants are offline or behave maliciously, the system can still operate normally or detect fraud, ensuring high availability.
Privacy Payment and Settlement
In the financial sector, MPC can be used for privacy-preserving settlement between institutions or on consortium blockchains. Parties can use encrypted transaction data as input to jointly compute settlement results, risk exposures, or credit limits without revealing the underlying transaction details to other collaborators. This enables institutions to conduct necessary financial collaboration while maintaining data sovereignty.
Anti-Money Laundering (AML) Collaboration
MPC has significant potential in compliance. Banks and regulatory authorities can jointly run complex analytical models using MPC, for example, to detect cross-institution money laundering or fraud patterns. The key is that this process can be completed without sharing customer transaction records or revealing sensitive data. MPC ensures that only the analysis results are output, while the raw input data remains confidential.
For example, BenFen’s MPC solution provides practical tools for AML and compliance analysis. Its platform supports multiple financial institutions in jointly running complex AML models through MPC protocols, such as cross-institution transaction pattern analysis, to detect potential money laundering or fraudulent activities, without sharing the original transaction data.
Comparative Advantages of MPC over Other Technical Approaches
To understand the strategic positioning of MPC, it is necessary to clearly distinguish it from other mainstream Privacy-Enhancing Technologies (PETs):
- MPC vs FHE: The design goal of MPC is to enable general computation on shared secret information among multiple participants; the design goal of FHE is to allow a single data owner to outsource encrypted data to an untrusted server for arbitrary computation.
- MPC vs ZKP: MPC is a general-purpose computation tool capable of computing any function; ZKP is a verification tool, whose output is a Boolean value, used only to prove the truth of a statement without revealing additional information.
- TEE’s Uniqueness: TEE does not rely on cryptographic protocols but instead depends on hardware-isolated regions provided by processor manufacturers, where plaintext computation occurs inside the enclave.
Performance Comparison
Comparison of Metrics: Computation Overhead and Communication Cost
Performance is a key factor determining whether PETs can be deployed in real-time financial applications. The following compares the technologies in terms of computation overhead, latency, communication cost, and integration difficulty.
Computation Overhead and Latency
Although FHE offers theoretical maximum flexibility, it comes at an extremely high computational cost. FHE’s computation speed is 10,000 to 100,000 times slower than plaintext computation, and this high latency and cost make it difficult to deploy in applications sensitive to real-time performance and cost.
In contrast, MPC has much lower computation overhead and is generally faster than FHE in practice. In terms of latency, TEE approaches native execution, with the lowest latency; MPC has medium-to-low latency, but is highly affected by network communication conditions; FHE has the highest latency due to frequent bootstrapping operations. For privacy payment services that require real-time response, FHE’s high latency is a significant engineering barrier, whereas MPC provides a practical medium-to-low latency solution.
Communication Overhead and Integration Difficulty
The main technical weakness of MPC is communication overhead. MPC protocols require frequent, intensive interactive communication between participating nodes. As the number of participants (N) increases, communication cost and synchronization issues rise sharply, becoming a bottleneck. In contrast, FHE requires relatively less data transmission in client-server models.
Regarding integration difficulty: TEE projects have the lowest barrier, requiring minimal changes to existing programming models; MPC, ZKP, and FHE all have higher integration complexity. Among them: ZKP and FHE usually require specialized circuit design and compilation; MPC requires complex protocol stack integration and cross-node communication architecture design.
Scalability Analysis: Natural Horizontal Scalability of MPC and ZKP
Scalability is a key factor in determining whether an infrastructure can support large-scale applications. MPC and ZKP demonstrate obvious architectural advantages, as they naturally support horizontal scaling. MPC can achieve this through sharding techniques, while ZKP achieves it via Rollup mechanisms. This means the system can linearly increase processing capacity by adding more general-purpose computation nodes, which is highly consistent with the modern trends of cloud computing and distributed systems.
In contrast, the scalability of FHE and TEE is limited by computational resources and the availability of specialized hardware nodes. For example, TEE deployment is constrained by hardware memory capacity and side-channel attack risks, while FHE requires enormous computational resources. Software- and cryptography-based MPC and ZKP align better with the demands of decentralized systems for resilience, general-purpose hardware, and open extensible models. Therefore, choosing MPC represents a long-term investment for future large-scale, decentralized infrastructure, avoiding hardware dependency and potential centralization risks associated with TEE.
Robustness and Fault Tolerance: MPC’s (t, n) Security Model
MPC protocols are designed with built-in fault tolerance. Based on secret-sharing (t, n) threshold mechanisms, the system can tolerate up to t faulty participants while still ensuring correct computation, or at least detecting malicious behavior in time. This intrinsic robustness makes MPC particularly suitable for financial services requiring high availability and secure custody of funds.
Conclusion and Prospect
The Optimal Balance Point of MPC Between Functionality, Performance, and Decentralization
The core reason for choosing MPC is that it achieves the best engineering balance between practicality, security, and decentralization. Although FHE theoretically offers the strongest privacy protection, its extremely high computational latency makes it infeasible for most real-time or near-real-time applications, especially in high-frequency financial transactions. MPC provides “good enough” privacy guarantees and “fast enough” performance, effectively meeting the demands of high-throughput financial systems.
In terms of critical trust models, MPC’s distributed cryptographic trust model is irreplaceable for Web3 and decentralized finance. In scenarios requiring the highest trust assurances, such as key management and asset custody, relying on a single hardware manufacturer’s TEE architecture introduces strategic centralization and censorship risks, making it unacceptable. MPC is the only solution that satisfies decentralization, high security standards, and practical performance requirements.
Collaborative Strategy of MPC with Other PETs: Building a Hybrid Security Architecture
The strategic recommendation is to adopt a hybrid security architecture, using MPC as the core computation layer while coordinating with other technologies:
- MPC as the Core Computation Engine: Execute critical, high-frequency, multi-party secure computation tasks, such as TSS signing, joint risk model execution, and privacy-preserving settlement.
- ZKP as the Verification and Integrity Layer: When handling large-scale data or Layer 2 scaling, leverage ZKP’s conciseness and verifiability to validate the correctness of MPC-delegated computations, enhancing system trustworthiness.
- FHE as the Auxiliary Computation Layer: Consider FHE’s remote outsourcing capability only for extremely complex, long-running computations or model training on a single data source.
Strategic Recommendation: MPC’s Core Role in Future Privacy Payment Infrastructure
Based on its continuously improving efficiency over the past decade, proven commercial feasibility, and support for natural horizontal scaling architectures, this report recommends Multi-Party Computation as the key core technology for next-generation privacy payment infrastructure. Future R&D resources should focus on further optimizing communication overhead in MPC protocols, and through innovative protocol design, improve performance in large-scale, high-concurrency collaborative scenarios, thereby consolidating MPC’s strategic core position in the field of privacy computation.
BenFen Privacy Payment: Practical Integration of MPC with On-Chain Applications
In practice, the BenFen public blockchain, through deep collaboration with the core infrastructure builder TX-SHIELD, has natively embedded MPC-based privacy solutions at the chain layer, providing high-security payment solutions for both users and institutions. BenFen, leveraging Move VM, natively supports private accounts and privacy-preserving payments, allowing users to hide transaction amounts and account balances on-chain. Combined with stablecoin-based gas payments and sponsored transaction mechanisms, it optimizes convenience and usability of on-chain operations.
BenFen’s privacy payments and MPC technology complement each other: under the multi-party threshold signature (TSS) framework, key shares of user assets are distributed across different nodes, and transaction signing occurs without exposing any private key in plaintext, ensuring both asset security and transaction privacy. In the future, BenFen will continue to advance a more decentralized SMPC approach, enhancing censorship resistance and fault redundancy, further strengthening the robustness of its privacy payment system.
The application layer entry point, BenPay, truly brings BenFen’s privacy payment capabilities into the user experience layer: Stablecoins can be used directly to pay gas fees, allowing users to maintain privacy throughout their DeFi Earn,BenPay Card multi-chain deposits, cross-border payments, and on-chain transfers. They do not need to hold native tokens and can participate in Web3 financial operations in a more familiar and low-friction way.

In BenPay DeFi Earn, users’ position changes and strategy adjustments are not exposed to third-party on-chain analytics. In BenPay Card, the transaction path from on-chain assets to offline spending is protected by privacy mechanisms, preventing consumption behaviors from being tracked. During cross-chain operations, transfers, or asset management processes, sensitive records do not form identifiable, traceable transaction trails, enabling on-chain financial activities to achieve a level of security and freedom comparable to cash payments.
Through collaboration with TX-SHIELD, BenFen not only delivers a high-performance, high-availability, privacy-preserving stablecoin settlement solution for enterprise users, but also demonstrates the practical potential of MPC and sets a technical benchmark for the next-generation privacy payment system.

